Chapter5 - The internet and its uses
5.01 The internet and World Wide Web (WWW)
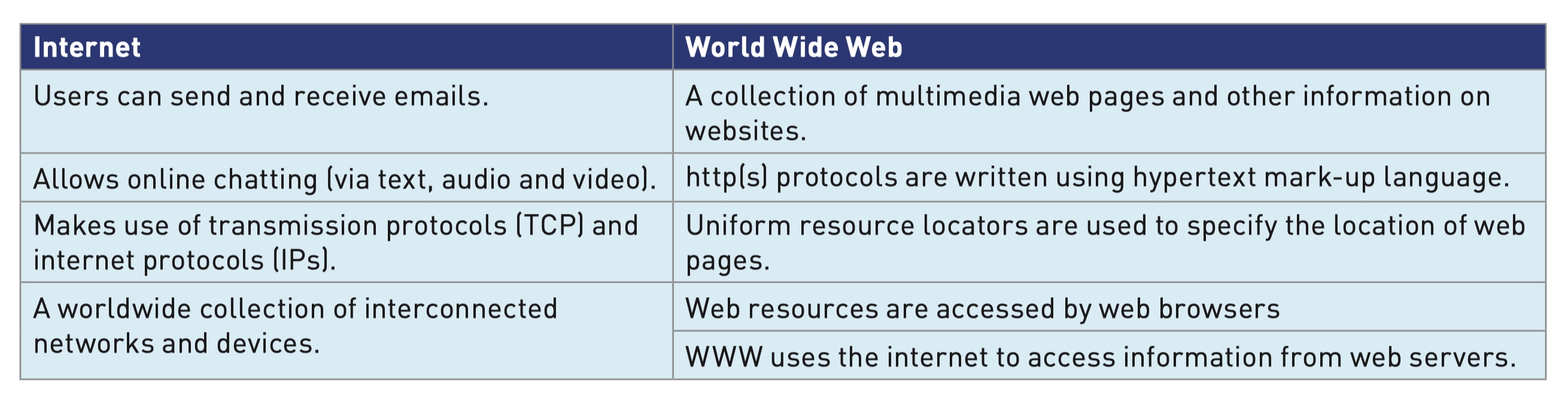
Differences between the internet and World Wide Web (WWW)
Uniform resource locators(URL)
Web browsers (often simply referred to as ‘browsers’) are software that allow users to access and display web pages or play multimedia from websites on their devices.
The browser interprets hypertext mark-up language (HTML) sent from the websites.

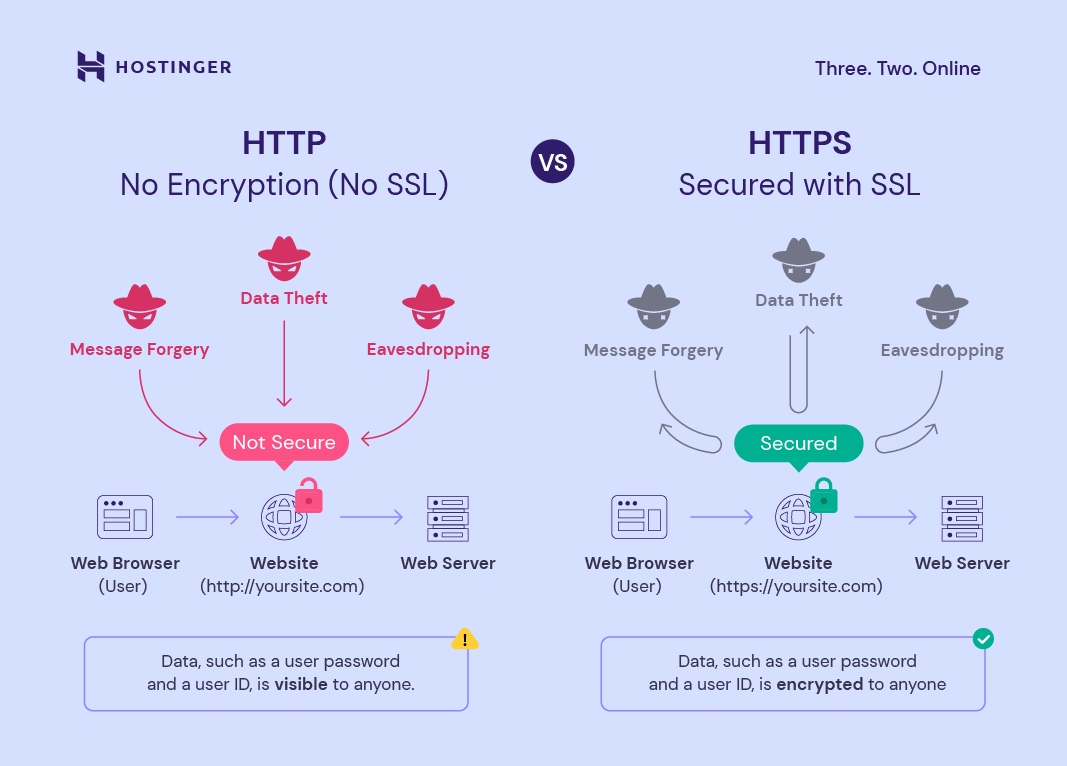
http and https
Hypertext transfer protocol (http) is a set of rules that must be obeyed when transferring files across the internet.
Https = http + secure
Web browsers
The main features of a typical browser::
- a home page and address bar
- the ability to store favourite websites and web pages (bookmarks)
- keeping a history of websites visited (user history)
- the ability to allow the user to navigate forwards and backwards through a website
- allowing many web pages to be open at the same time by using multiple tabs
- making use of cookies
- using hyperlinks to navigate between websites
- data stored as a cache
- make use of JavaScript.
5.02 The internet and the world wide web continued
Retrieval and location of web pages and websites
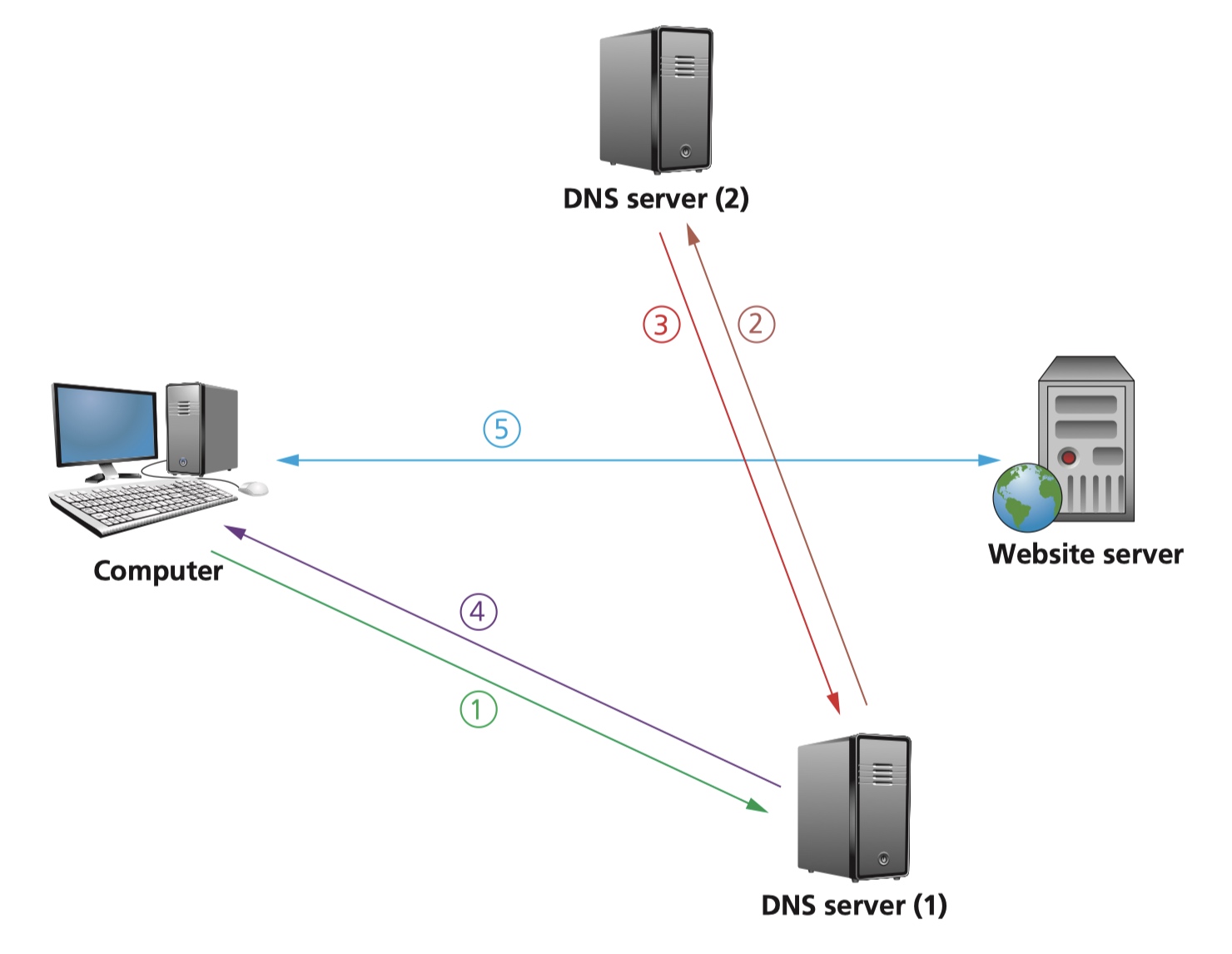
To retrieve pages from a website, a browser needs to know the IP address. A domain name server (DNS) is used to find the IP address from the domain name in the URL typed into the browser window.
- The user opens their browser and types in the URL (www.hoddereducation.co.uk) and the browser asks the DNS server (1) for the IP address of the website.
- In this case, let us assume the DNS server can’t find www.hoddereducation.co.uk in its database or its cache, so it sends out a request to DNS server (2).
- The DNS server (2) finds the URL and can map it to 107.162.140.19; this IP address is sent back to the DNS server (1) which now puts this IP address and associated URL into its cache/database.
- This IP address is then sent back to the user’s computer.
- The computer now sets up a communication with the website server and the required pages are downloaded. HTML files are sent from the website server to the computer. The computer’s browser interprets the HTML, which is used to structure content, and then displays the information on the user’s computer.
Cookies
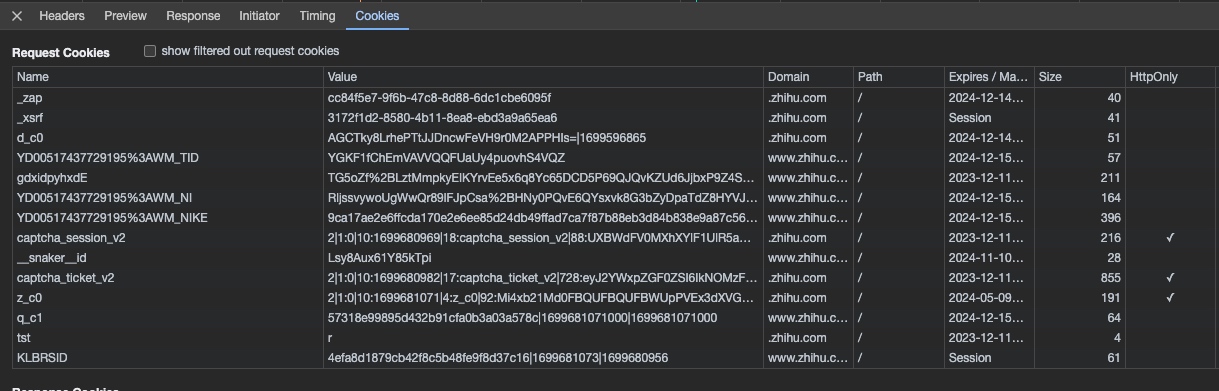
Cookies are small files or code stored on a user’s computer (permanently or temporarily). Cookies are sent by a web server to the browser on a user’s computer.
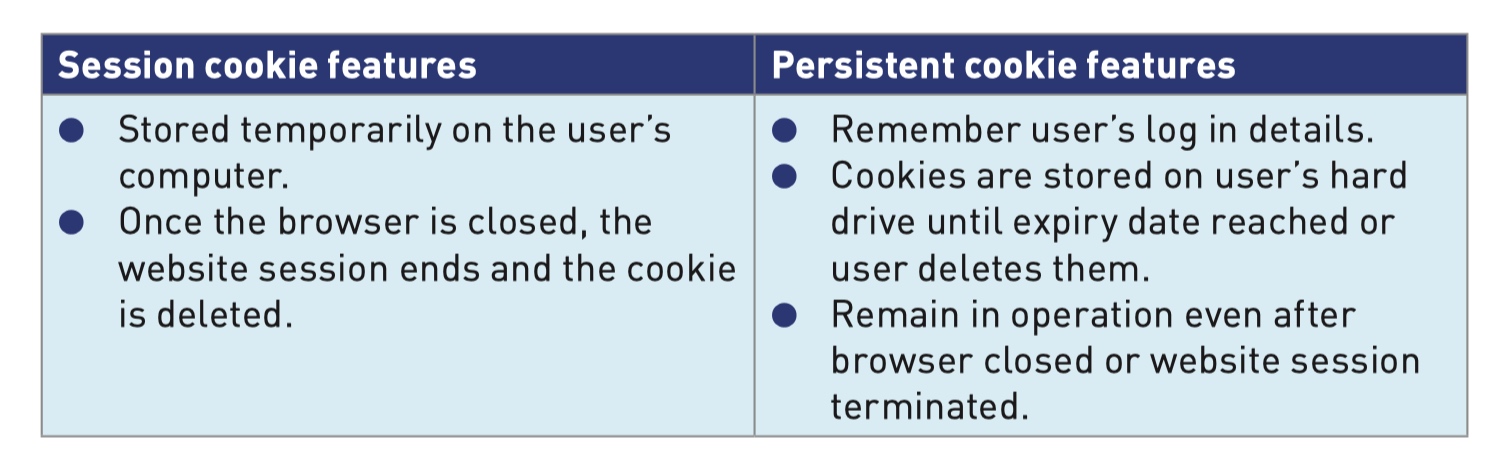
Session cookies
- Used for making online purchases.
- Used for virtual shopping baskets.
- Stored temporarily only for the single website session and are deleted when the user leaves the website.
- Don’t collect and information about the user and don’t identify who they are.
Persistent cookies
- Allow websites to remember user passwords, email addresses and so on; permitting faster log in.
- Serve as a memory, enabling the website to recognise users every time they visit the website.
- Save user’s items in a virtual shopping basket/cart.
- Track user’s browsing habits and website history.
- Allow targeting of specific users with advertising based on previous buying/surfing habits.
- Storing user preferences.
- Used in online transactions.
- Allow social networking sites to recognise certain preferences and browsing history.
- Allow different languages to be used on the web pages automatically as soon as users log in.
5.03 Digital currencies
Digital currencies

Digital currency exists purely in a digital format and has no physical form unlike fiat currency (for example, £, $, €, ¥). It relies on a central banking system (centralisation); however, this makes it difficult to maintain confidentiality and security.
Cryptocurrency is a type of digital currency that overcomes security and confidentiality issues.
Cryptocurrency uses cryptography to track transactions; the use of cryptography was introduced to address the security problems sometimes associated with the centralisation of digital currency.
Blockchaining
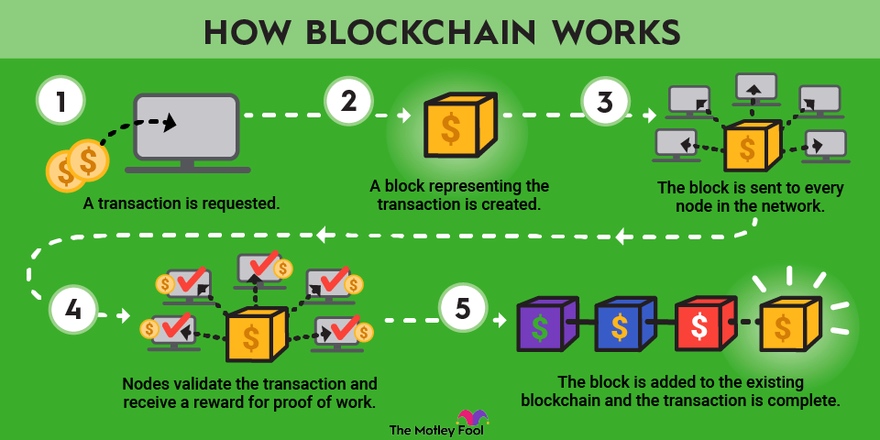
Cryptocurrency makes use of blockchaining. Blockchain is a decentralised database; when a new transaction takes place, all networked computers in the system get a copy of the transaction, removing security risks such as hacking.
block::
- data
- a new hash value (a unique value generated by an algorithm)
- a previous hash value pointing to the preceding block
The hash value is unique to each block and includes a timestamp, which identifies when the creation of the block took place.
In a blockchain the first block is called the genesis block.
Apart from cryptocurrency, other uses of blockchain include::
- smart contracts
- in research – for example, development of new drugs
- in politics
- in many areas of education.
5.03 Cyber security
Cyber security threats
cyber security threats::
- brute force attacks
- data interception
- distributed denial of service (DDoS) attacks
- hacking
- malware
- phishing
- pharming
- social engineering.
Brute force attacks

A brute force attack is a method where all combinations of letters, numbers and other symbols (such as !, &, @) are tried to generate passwords.
The method relies on the high speed of computer processing, therefore longer, more complex, passwords make the task of the cybercriminal much harder.
There are ways brute force attack criminals try to make cracking passwords an easier task::
- check if the password is in a list of commonly used passwords (such as, 123456, ABCD123, querty, and so on)
- if it isn’t a common password, the criminal can then check a word list (this is a text file containing a collection of words that have been used in passwords by certain groups of people or organisations) – while the word list can still be very long, they do save a lot of time.
Data interception
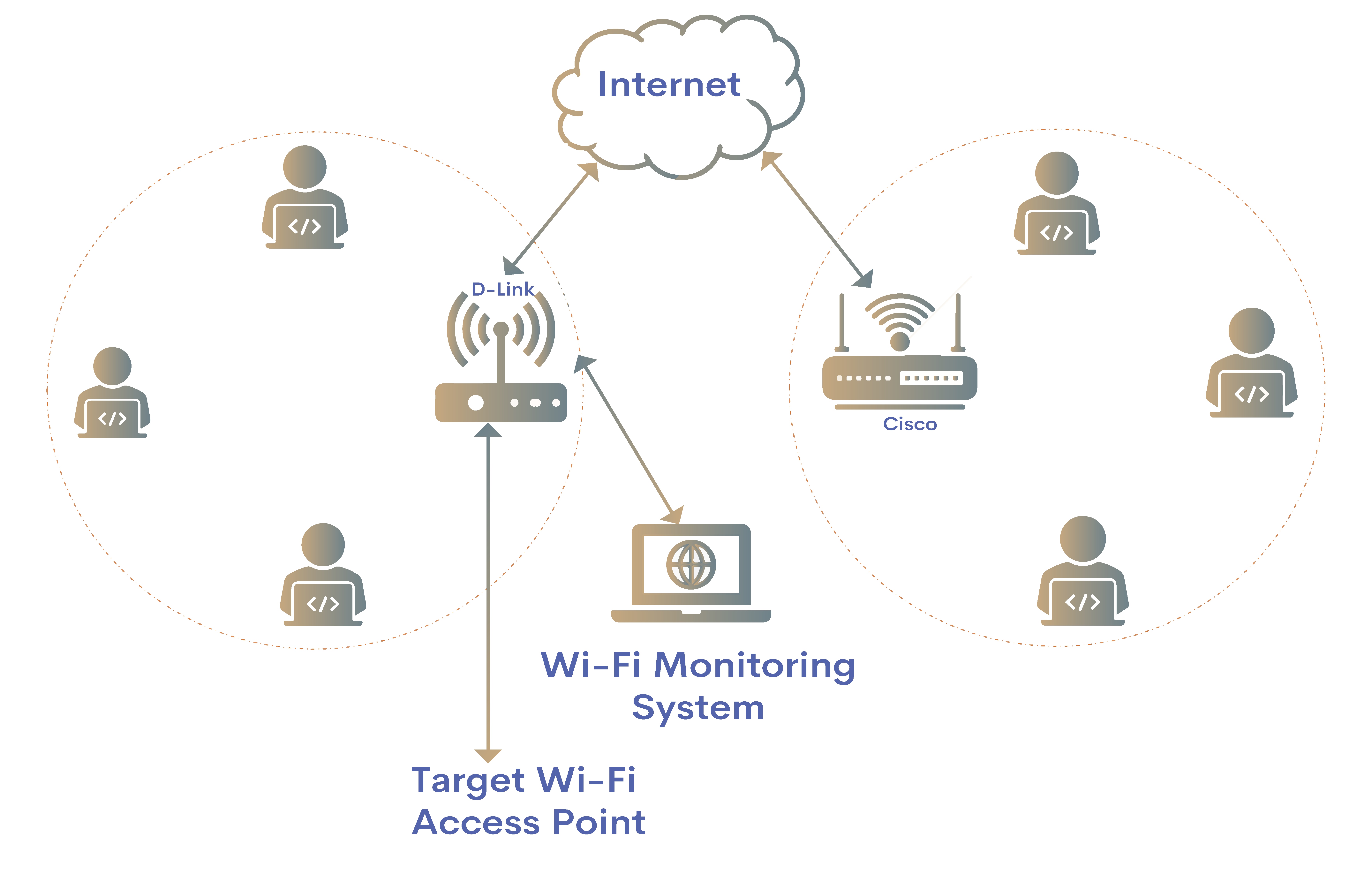
Data interception is the stealing of data by tapping into a network.
packet sniffers:: examine all data packets on a network and read the data being moved across the networks.
War driving (also known as access point mapping) is a method that intercepts Wi-Fi (wireless) signals; the method requires a laptop, smartphone or tablet, an antenna, a GPS device, and software to gather the data from the wireless network.
Wired Equivalency Privacy (WEP) encryption protocol is used – this gives a wireless LAN the same level of security as a wired network.
Distributed denial-of-service attacks
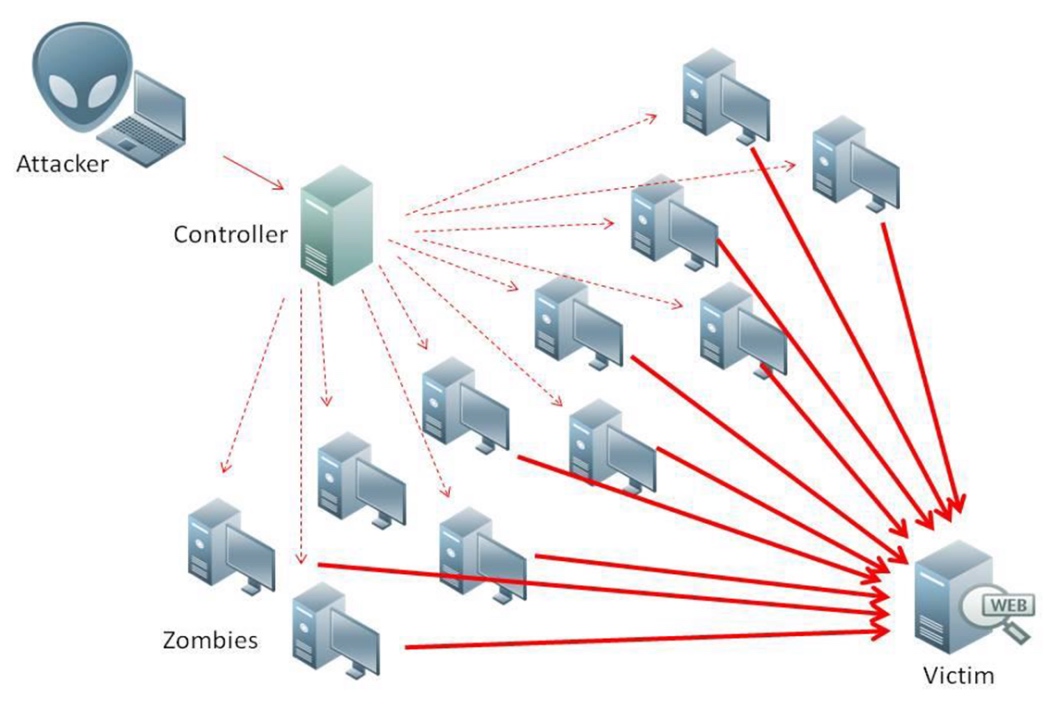
distributed denial-of-service (DDoS) attack is an attempt to prevent anyone accessing part of a network.
It is slightly different to a denial-of-service (DoS) attack, which only uses a single computer to carry out the attack;
DDoS can also be used to attack an individual’s computer by preventing them accessing their emails, certain websites or online services.
It is possible to mitigate the risk of DDoS by using up-to-date malware checkers, ensuring there is a firewall running to filter out spam and applying email filters to filter out unwanted traffic.
Hacking
Hacking is gaining illegal access to a computer system without the user’s permission.
It can lead to identity theft, gaining personal information or the loss/corruption of key data.
prevent::
- firewall
- usernames
- frequency changed strong passwords
- anti-hacking software
ethical hacking:: companies employ staff to try and hack into their systems to check how strong their security measures are.
Malware
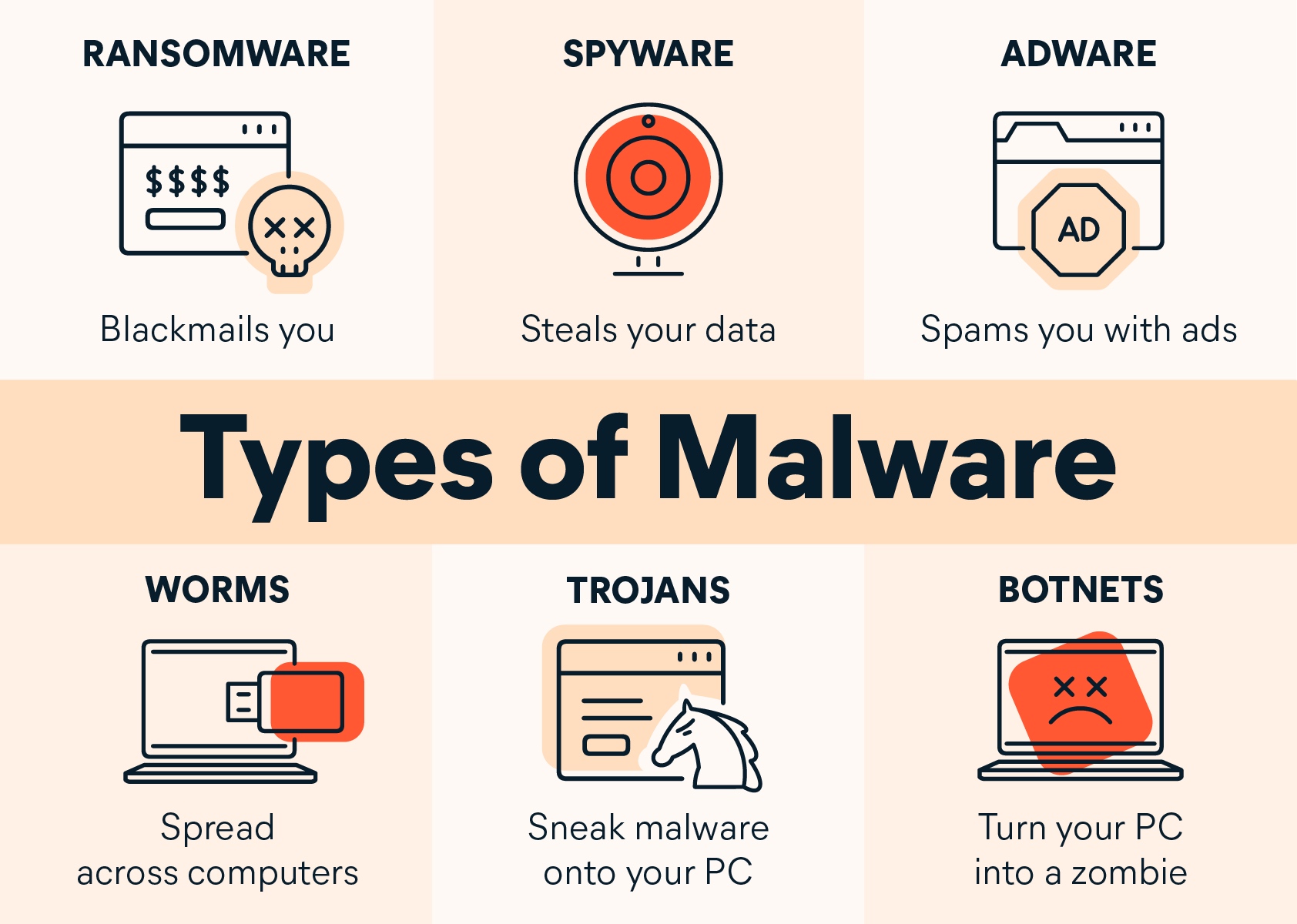
- Viruses are programs (or program code) that can replicate or copy themselves with the intention of deleting or corrupting files, or causing the computer to malfunction.
- Worms are types of stand-alone viruses that can replicate themselves with the intention of spreading to other computers.
- Trojan horses are malicious programs often disguised as legitimate software. They replace all or part of the legitimate software with the intent of carrying out some harm to the user’s computer system.
- Spyware is software that gathers information by monitoring.
- Adware is software that floods a user’s computer with unwanted advertising, usually in the form of pop-ups.
- Ransomware are programs that encrypt the data on a user’s computer, so a decryption key is needed.
Phishing
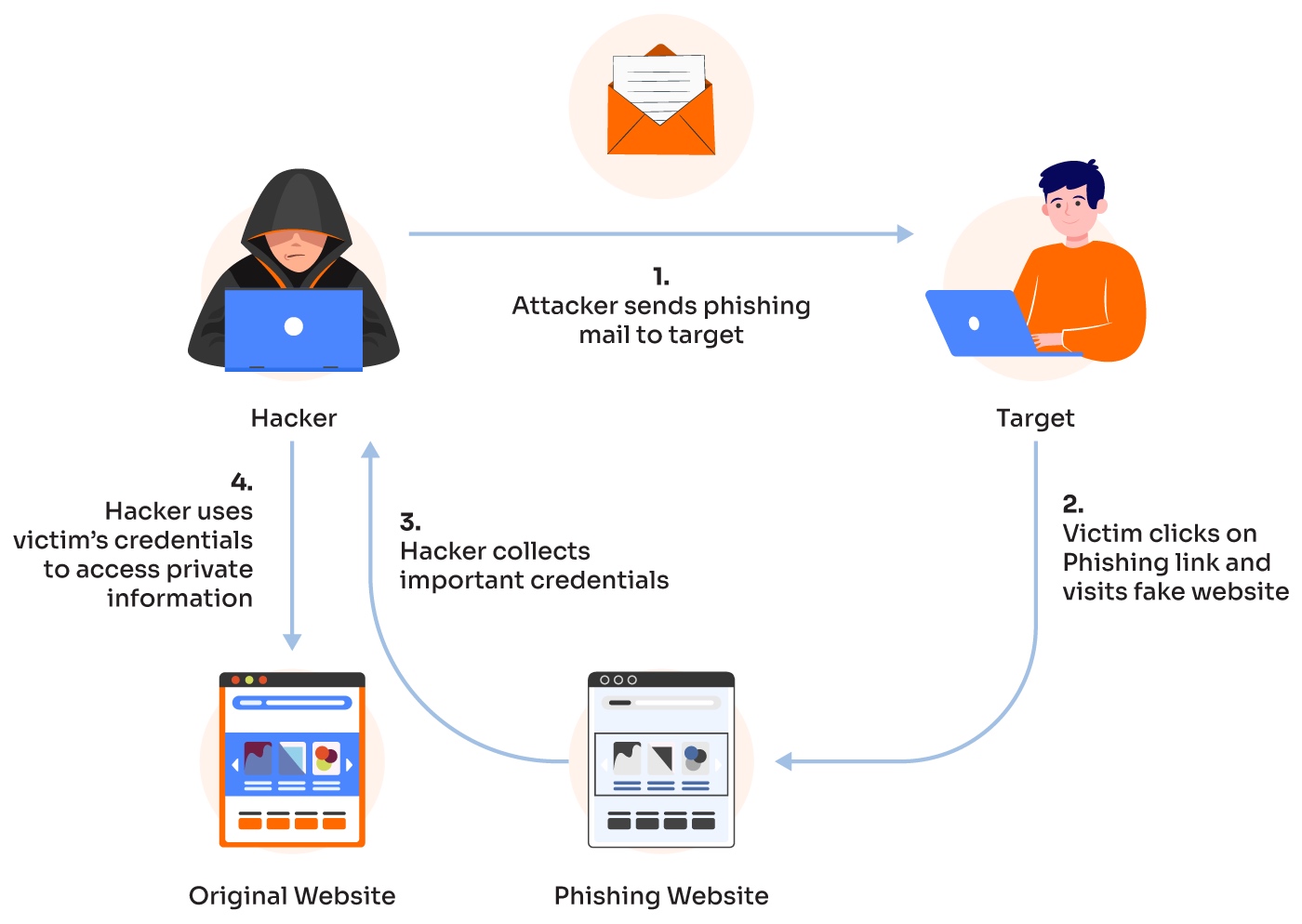
Phishing is the sending out of legitimate-looking emails to users; they may contain links to or attachments to fake websites.
They require the user to take some action to initiate the phishing attack
spear phishing – a cybercriminal targets specific individuals/companies to get access to financial data or for industrial espionage.
How to prevent::
- awareness training of users
- not clicking on links in emails unless you are 100% certain they are genuine
- running the anti-phishing tool in the browser
- using up-to-date browsers and run up-to-date firewalls
- closing down ‘pop-ups’ by selecting the small ‘x’ in the top right corner
- getting information about the email sender by clicking on the information symbol (a letter ‘i’ in a small circle); the actual email address from the sender will indicate whether or not it is from a genuine source.
Pharming
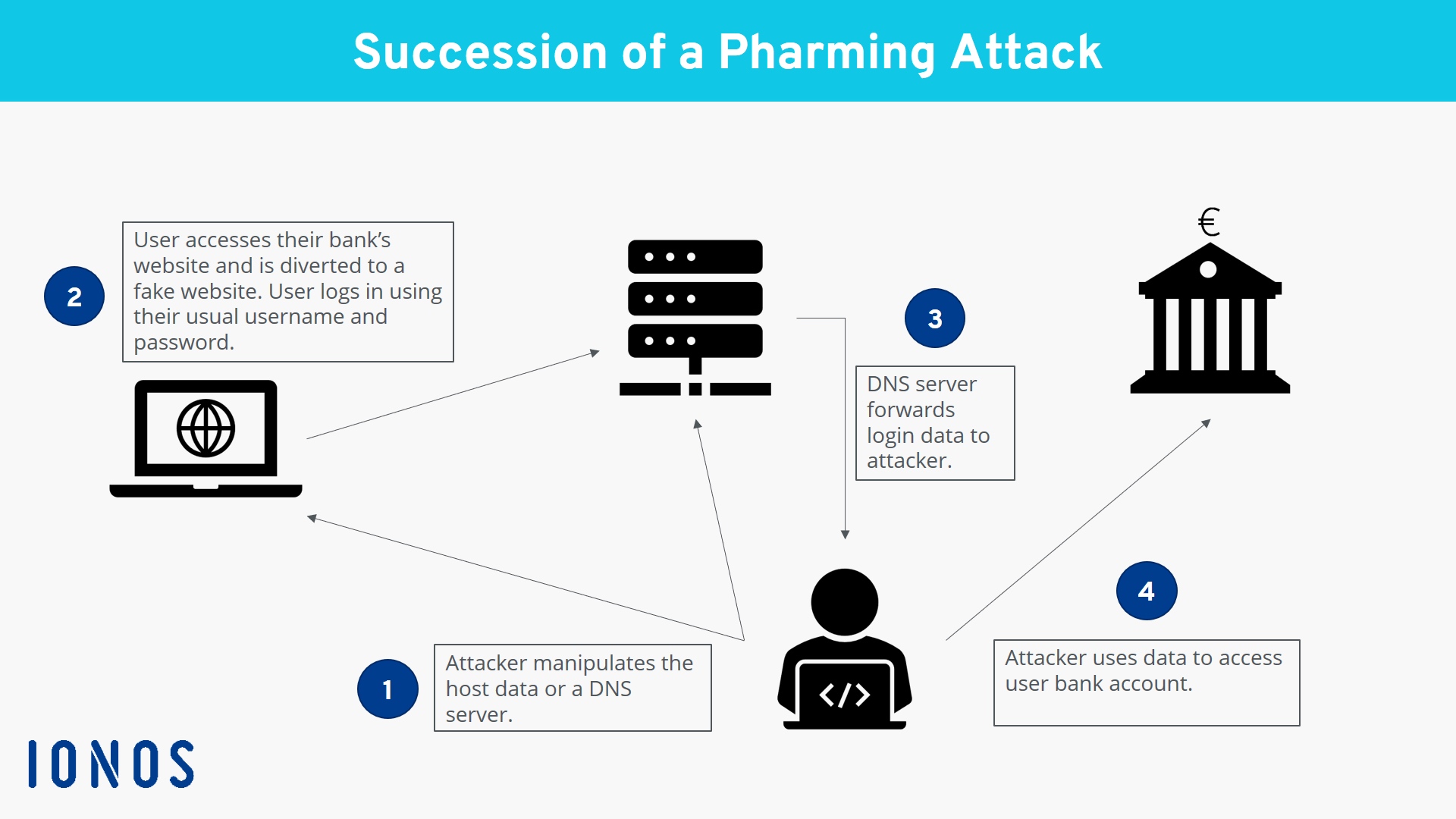
Pharming is malicious code installed on a user’s computer or web server without their knowledge.
The creator of the malicious code can gain information by sending the user’s browser to a fake website without their knowledge.
Pharming redirects the user’s browser to a fake/malicious website often by using DNS cache poisoning
How to prevent::
- modern browsers alerting the user to potential phishing and pharming attacks
- running up-to-date virus checkers which will look for malicious code stored on the user’s computer or on the web server
- checking the spelling of websites (for example, Amozon) to see if they are genuine
- getting information about the email sender by clicking on the information symbol (a letter ‘i’ in a small circle); the actual email address from the sender will indicate whether or not it is from a genuine source.
Social engineering
Social engineering occurs when a cybercriminal creates a social situation that can lead to a potential victim ‘dropping their guard’.
threats::
- Instant messaging: Malicious links are embedded into instant messages, for example an important software upgrade (relies on user’s curiosity).
- Scareware:: pop-up message that claims that the user’s computer is infected with a virus(fake antivirus that looks real)
- Emails/phishing scams:: apparent genuineness of an email and opens a link in the email, redirects their browser to a fake website
- Baiting:: leaves a malware-infected memory stick
- Phone calls:: so-called IT professional calls the user on their mobile claiming their device has been compromised in some way
exploited::
- Fear:: The user is panicked into believing their computer is in immediate danger and is not given time to logically decide if the danger is genuine or not.
- Curiosity:: Without thinking clearly, their curiosity gets the better of them and the damage is done.
- Empathy and trust:: A belief that all genuine-sounding companies can be trusted.
Keeping data safe from security threats
Use of access levels
User accounts can be used to control a user’s rights.
This involves a number of levels of access, each protected by a username and password.
Access levels are used by social network sites in privacy settings to protect a user against potentially dangerous activity.
Anti-malware
Anti-spyware software method::
- Rules – looks for certain features associated with spyware.
- File structures – looks for file structures common to spyware software.
anti-spyware features::
- Detects and removes spyware from user’s HDD/SSD.
- Prevents the downloading of spyware.
- Encrypts files making data more secure in case spyware becomes installed on user’s computer.
- Encrypts keyboard strokes.
- Blocks access to user’s webcam and microphone if suspicious activity detected.
- Scans for signs that the user’s personal information is being stolen and warns the user.
Authentication
Authentication refers to the ability of a user to prove who they are.
three factors used in authentication::
- Something you know (for example, a password or PIN).
- Something you have (for example, a mobile phone or tablet).
- Something unique to the user (for example, biometrics).
Passwords features::
- be changed regularly
- not be easy to guess (for example, date of birth is a very weak password)
- be strong (at least eight characters including numbers, lower case letters, upper case letters and other keyboard symbols, for example, T7%%asR3£Sc is very strong but pas5word is very weak).
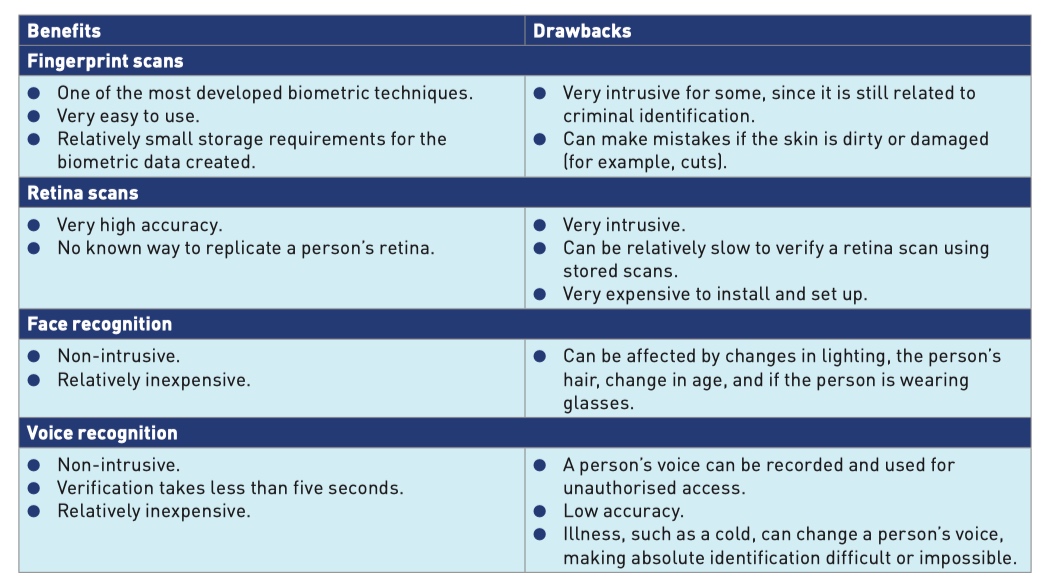
Biometrics
Biometrics can be used as a type of password and are based on certain unique human characteristics
- fingerprint scans
- retina scans
- face recognition
- voice recognition.
Applications of biometrics::
- door security systems
- some mobile phones use fingerprint scans and/or face recognition, rather than a PIN, to unlock the phone for use.
Two-step verification
Two-step verification is used as a method of authentication where two different types of authentication are needed to identify someone.
- a user logs onto a website using username and password and decides to use their credit card to buy something
- as part of the security, an 8-digit PIN is sent back to the user either in an email or as a text message to a mobile phone number already registered on the website (this is known as a one-time pass code (OTP))
- this 8-digit PIN is entered on the website proving the user’s identity.
Automatic software updates
Automatic updates of software keep a device secure.
The updates will contain patches that could include updated virus checkers, software improvements and bug fixes.
Check spelling and tone of communication and of URL links
- Look out for suspicious links; destination address should match rest of the email
- Check the spelling in the email itself and any links.
- Check the tone of the message and language used.
- Check email addresses
Firewalls
Firewalls can be either software or hardware;
features::
- Examine the ‘traffic’ between the user’s computer and an external network (for example, the internet).
- Check if incoming or outgoing data meets certain criteria; if the data fails the criteria, the ‘traffic’ is blocked, and the user is given a warning that there may be a security issue.
- Can prevent access to certain undesirable websites; they keep a list of all undesirable IP addresses.
- Can help prevent viruses or hackers.
- Maintain a log so a user can interrogate the daily activity to and from their computer.
firewalls cannot prevent potentially harmful traffic::
- If individuals use their own hardware on networks and bypass the network’s firewall.
- Employee misconduct or carelessness (for example, poor control of passwords).
- Stand-alone computers can choose to disable a firewall allowing harmful traffic to enter the network.
Proxy servers
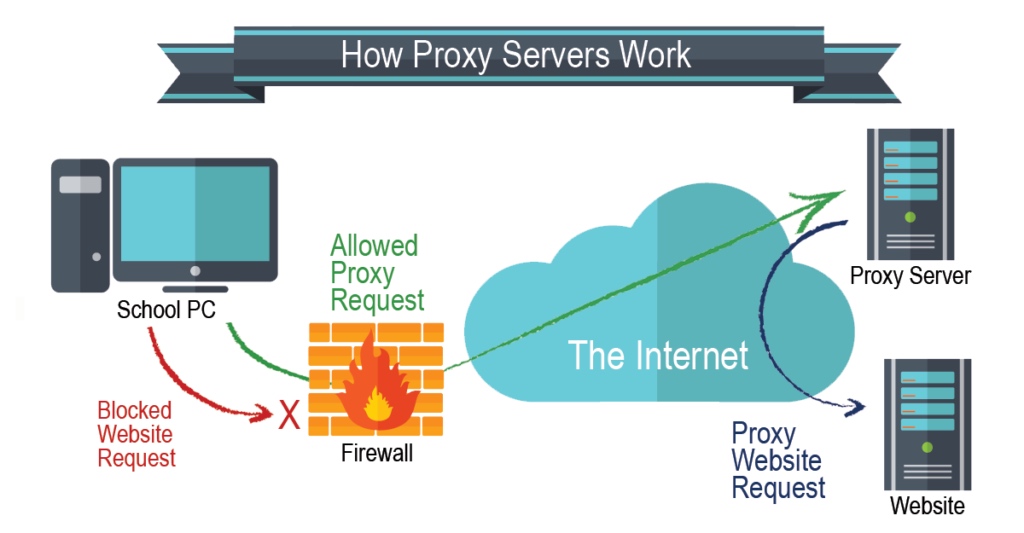
Proxy servers are an intermediate between a user and a web server.
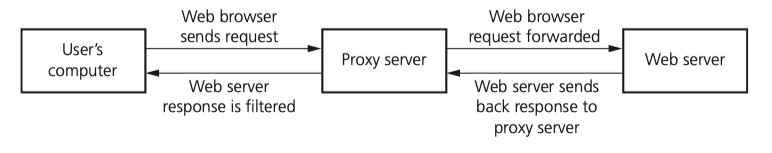
features::
- Filter internet traffic, blocking access to websites if necessary.
- Keep user’s IP addresses secret.
- Can block requests from certain IP addresses.
- Prevent direct access to a web server by sitting between user and server.
- If a cyberattack is launched, the proxy server is affected instead of the web server, thus leaving the web server secure.
- Can direct invalid traffic away from the server.
- Using a ‘cache’ speeds up access to a website; the website home page is stored in a cache on the proxy server – next time the user visits the website, the proxy server cache is first checked and the home page is found.
- Can act as a firewall.
Privacy settings
Privacy settings are controls available on web browsers, social networks and other websites; they are designed to limit who can access and see a user’s personal profile (data).
- a ‘do not track’ setting that stops websites collecting browsing data
- a check to see if the payment methods have been stored on websites, thus preventing the need to type in financial details each time a website is visited
- privacy options (browsing history, storing cookies)
- advertising opt-outs preventing unsolicited adverts from websites
- preventing apps sharing your location.
Secure sockets layer
Secure sockets layer (SSL) is a type of protocol used by computers to communicate securely with each other across networks.
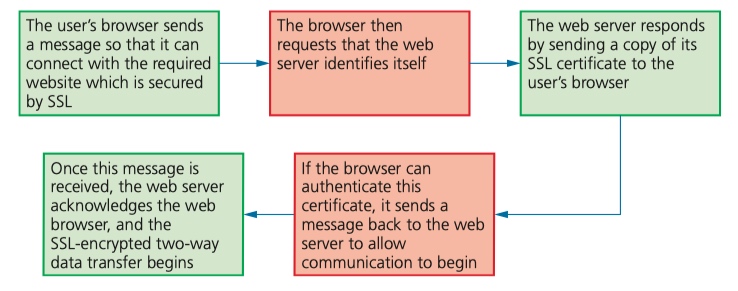
SSL certificates are a form of digital certification used to authenticate a website. SSL could be used when doing online banking, online shopping, sending/receiving emails, using cloud storage, using VoIP or instant messaging.