ALevel-CS Chapter 21
Security
21.01 Encryption fundamentals
Key Terms
- Plaintext - data before encryption
- Ciphertext - the result of applying an encryption algorithm to data
- Symmetric key encryption - one private key is held by both sender and receiver and is used for both encryption and decryption
- Asymmetric key encryption - there is a public key and a private key one of which is used for encryption and the other for decryption
Encryption fundamentals
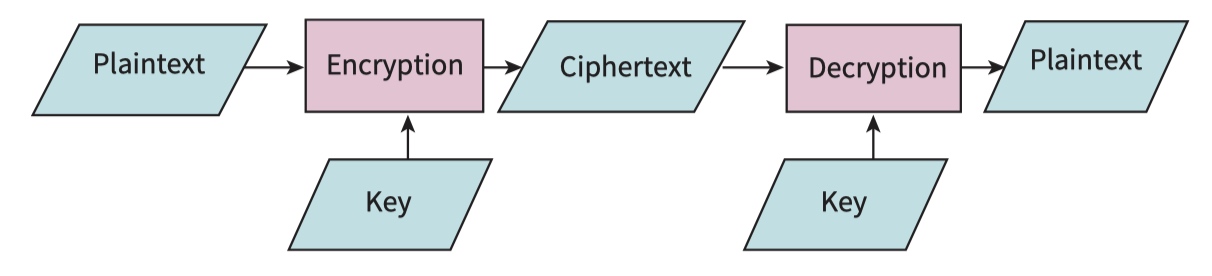
The process starts with original data referred to as plaintext, whatever form it takes. The plaintext is encrypted by an encryption algorithm which makes use of a key. The product of the encryption is ciphertext, which is transmitted to the recipient. When the transmission is received it is decrypted using a decryption algorithm and a key to produce the original plaintext.
Security concerns
security concerns relating to a transmission
- Confidentiality: Only the intended recipient should be able to decrypt the ciphertext.
- Authenticity: The receiver must be certain who sent the ciphertext.
- Integrity: The ciphertext must not be modified during transmission.
- Non-repudiation: Neither sender nor receiver should be able to deny involvement in the transmission.
- Availability: Nothing should happen to prevent the receiver from receiving the transmission.
加密算法
对称加密
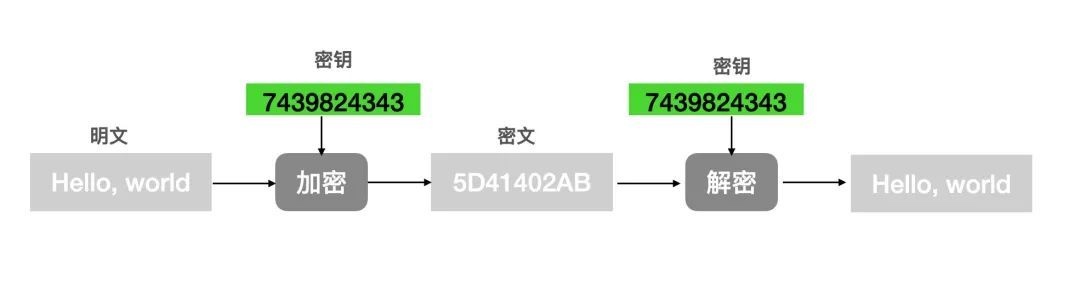
对称加密是指加密和解密时使用同一个密码
非对称加密
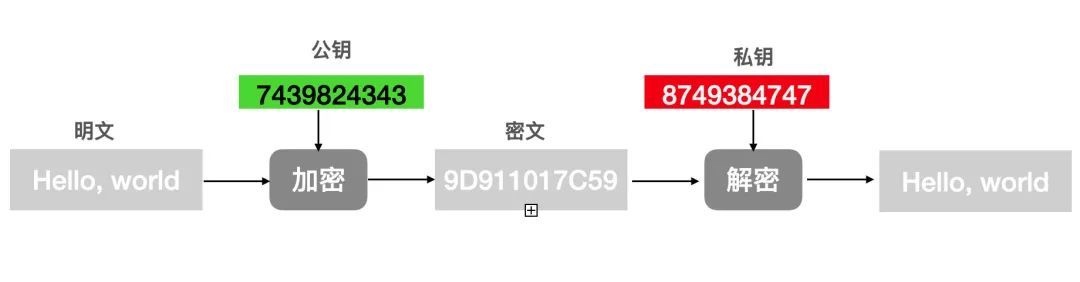 公钥加密私钥解密
公钥加密私钥解密
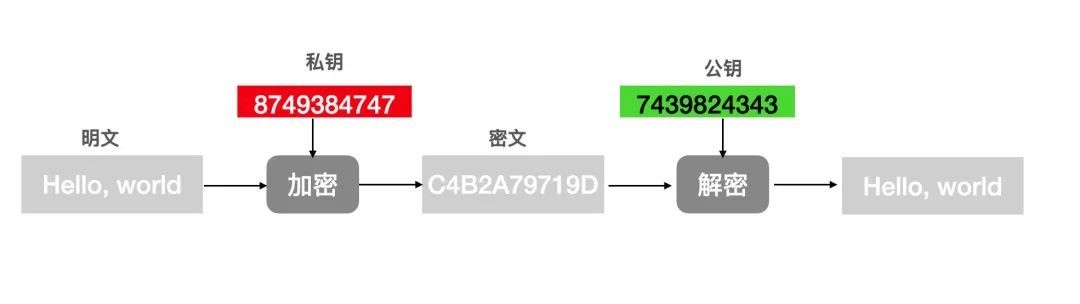 私钥加密公钥解密
私钥加密公钥解密
非对称加密是指加密和解密使用不同的秘钥,这两个秘钥分别叫做公钥、私钥。 公钥是可以公开给所有人的,私钥是要自己保密的。
密码的产生(第一回合)
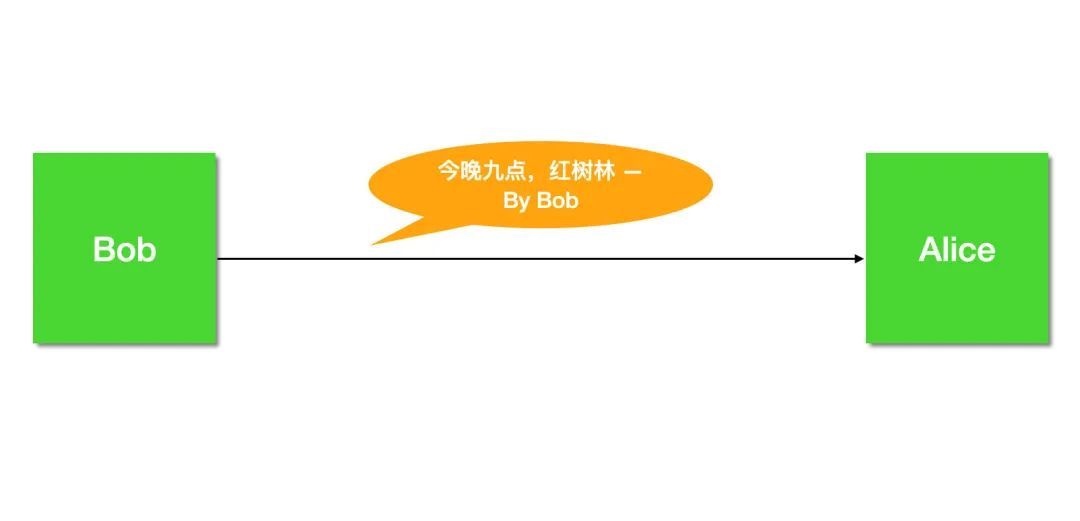
Alice 和 Bob,以及窃听者代表 Eve。
我们从 Alice、Bob 约会的故事展开,来讲讲其中暗藏着哪些危机,又是如何一步步化解的
九月,一个夜黑风高的晚上,Bob 想约 Alice 出来玩,于是给 Alice 发了一封邮件
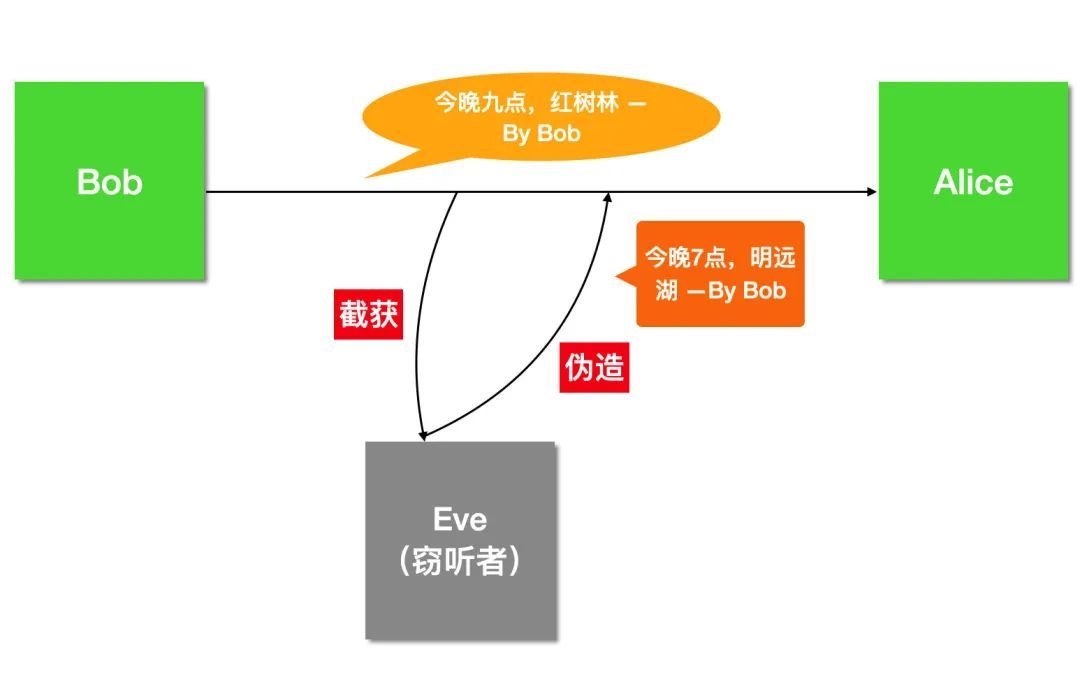
但我们都知道网络是不可信的,并且由于消息在网络中是明文传输的,所以黑客可以轻易的截获、篡改甚至冒充Bob。
黑客窃听伪造
瞧,Eve 轻易的拿到了邮件内容 (窃听),并且修改了邮件内容 (篡改),甚至说他可以随时冒充 Bob 给 Alice 发送邮件 (伪装)。
如果上图中 Eve 伪造的内容被 Alice 接收到了,那么后果可想而知。
现实世界中,我们每天都在通过网络进行聊天、转账、浏览不存在网站。
如果都是这样明文传输数据,显然毫无安全感。
第二回合
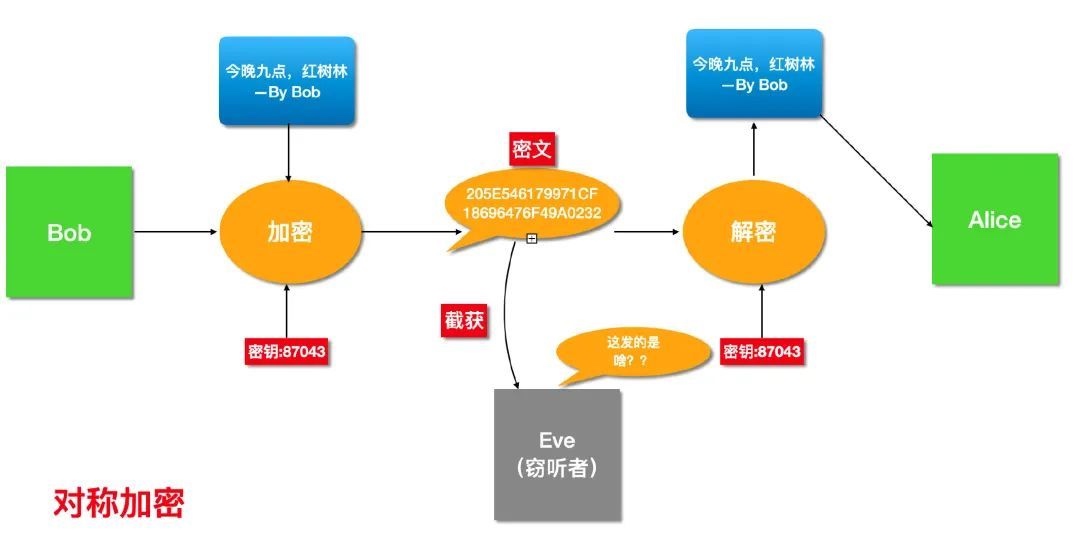
既然我们不能明文传输,那么 Bob 和 Alice 提前商量好密钥,使用对称加密对邮件内容加密不就好了~
只要 Bob 和 Alice 能够保证 密钥不泄露,整个通信就是安全的。
如果密钥泄露,被中间人截获,那么就等同于明文通信。
所以我们不能把安全性寄托在人上面。
并且这里也存在一个问题,如果两个人不能线下见面, 如何在网上安全的交换密钥呢?
这似乎是无解的,因为交换密钥的时候我们必须明文通信,不然对方根本看不懂。但是明文交换即意味着可能泄露。
但是别忘了我们的密码学工具箱里还有一个好东西— 「非对称加密」。
Bob 和 Alice 各自生成一对公私钥,因为公钥本来就是公开的,即可以被任何人获取,所以可以通过网络明文交换公钥。
然后使用公钥加密邮件内容后发送给对方,接收者使用自己的私钥即可解密。完美~
第三回合
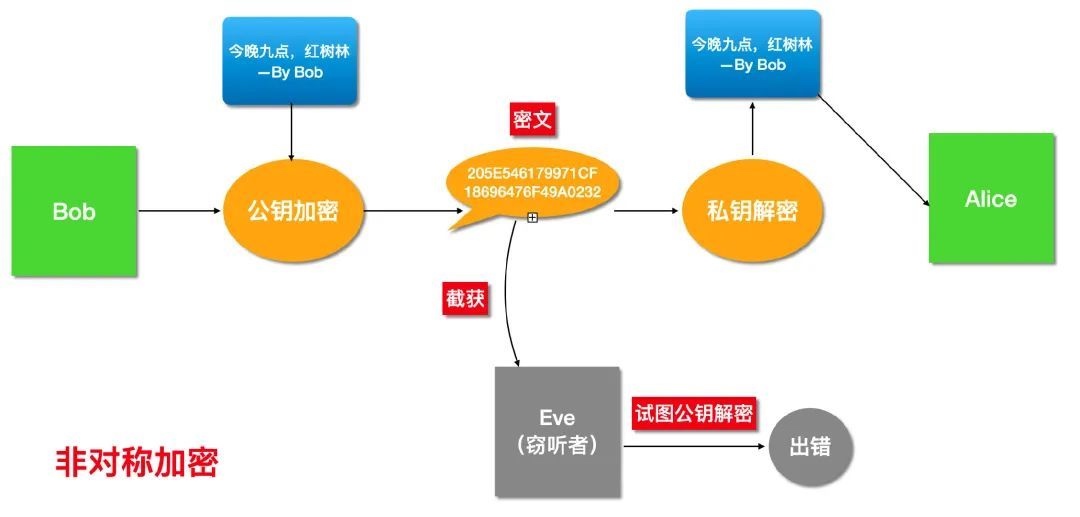
在非对称加密体系下,Bob 如何给 Alice 发消息的。
首先 Alice 需要先生成一对公私钥,私钥只能 Alice 自己知道,公钥是可以让任何人都知道的,因此可将公钥直接发送给 Bob,就算被截获也无所谓。
非对称加密
Bob 使用 Alice 的公钥加密邮件内容,加密后的内容只能由 Alice 的私钥解密,所以就算 Eve 截获也是徒劳。
反之,如果 Alice 想给 Bob 回信,就需要用 Bob 的公钥加密后发送。
这就解决了密钥交换问题,也保证了邮件内容不会泄露。也就是说现在可以防窃听。
如何证明Bob是Bob
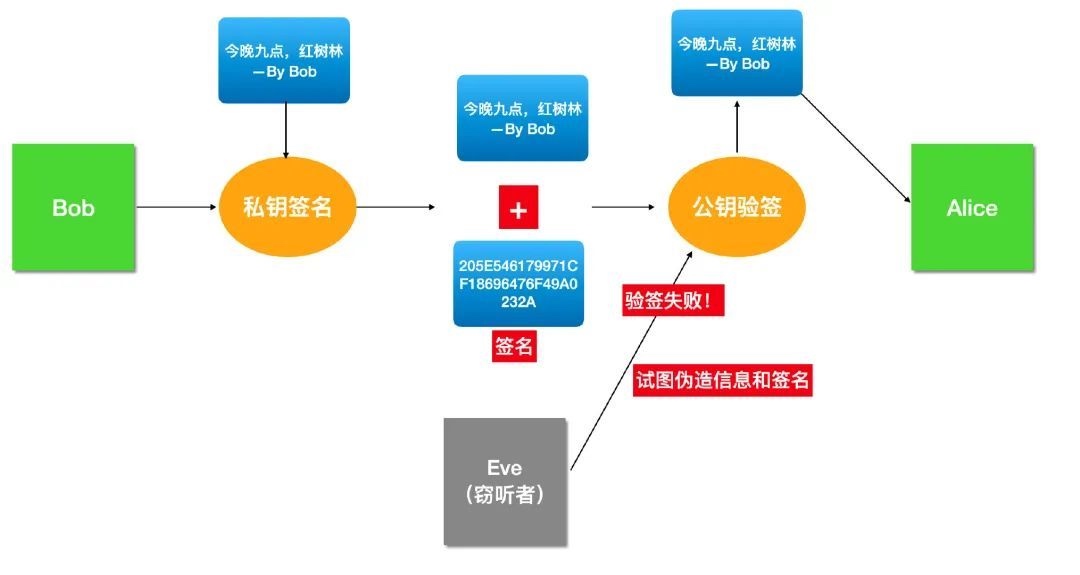
Eve 也可以使用 Alice 的公钥冒充 Bob 给 Alice 发邮件啊,因为 Alice 的公钥本来就是公开的,任何人都可以获得。
由于 Eve 也可以获得 Alice 公钥,所以没法防止 Eve 伪造和篡改,并且对于 Alice 而言,她无法分辨出邮件到底是 Eve 发的还是 Bob。
所以这个问题的本质就是 「Alice 如何确认邮件来自于 Bob」。
所以我们需要在计算机中引入类似的机制:
即只有 Bob 自己能够产生的独一无二的标志,并且其它人能够验证这个标志确实是属于 Bob的。
这就是「数字签名」。
就是 Bob 自己的私钥,Bob 用自己的私钥对邮件内容计算一个「签名」,将「签名」和邮件内容一起发送出去,接受者 Alice 可以使用 Bob 的公钥验证这个签名是否正确,这就叫「验签」。
如果不是 Bob 的私钥计算的签名,那么 Alice 用 Bob 公钥验签将会出错。
如何证明我就是我?
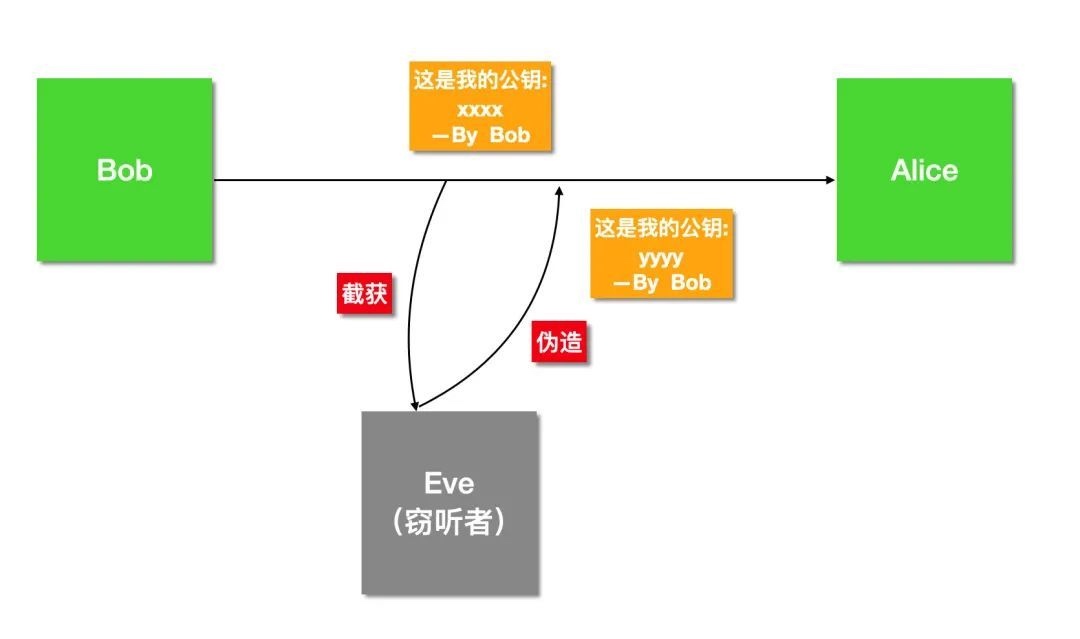
Bob 和 Alice 现在可以依赖于对称加密进行保密通信,也可以依赖于数字签名验证消息是否是对方发送的。
但是这一切的根基是建立在 Alice 持有的公钥确实是 Bob的,反之亦然。
Eve 如果将自己的公钥冒充 Bob 发送给 Alice,然后 Alice 保存了下来,那以后凡是 Bob 发送的消息,反而会验证签名失败,被当做冒充者。
数字证书
引入数字证书的目的是为了保证公钥不被篡改,即使被篡改了也能识别出来。
而防篡改的方法就是数字签名,但是这个签名不能我们自己做,原因说过了,因为我们的公钥还没分发出去,别人无法验证。
所以只能找可信的第三方来帮我们签名,即证书颁布机构(CA),CA 会将:证书的颁布机构、有效期、公钥、持有者(subject)等信息用 CA 的私钥进行签名。
并且将签名结果和这些信息放在一起,这就叫做「数字证书」。
收到 Bob 发过来的数字证书后,Alice 使用 CA 的公钥进行验证,验证通过即证明这确实是 Bob 证书,也就可以使用证书中包含的 Bob 的公钥,按照之前讨论的流程进行通信。
Encryption methods
there are two alternative approaches. One is symmetric key encryption, and the other is asymmetric key encryption also known as public key encryption.
In symmetric key encryption there is just one key. This key is a secret shared by the sender and the receiver of a message.
The issue with symmetric key encryption is delivery of the secret key.
In asymmetric key encryption two different keys are used, one for encryption and the other one for decryption. Only one of these is a secret.
pointer::
- If two people require two-way communication, both communicators need a private key and must send the matching public key to the other person.
- There are two requirements to ensure confidentiality should the transmission be intercepted and the message extracted:: the encryption algorithm must be complex and the number of bits used to define the key must be large.
21.02 Digital signatures and digital certificates
one-way hash function to send a digital signature
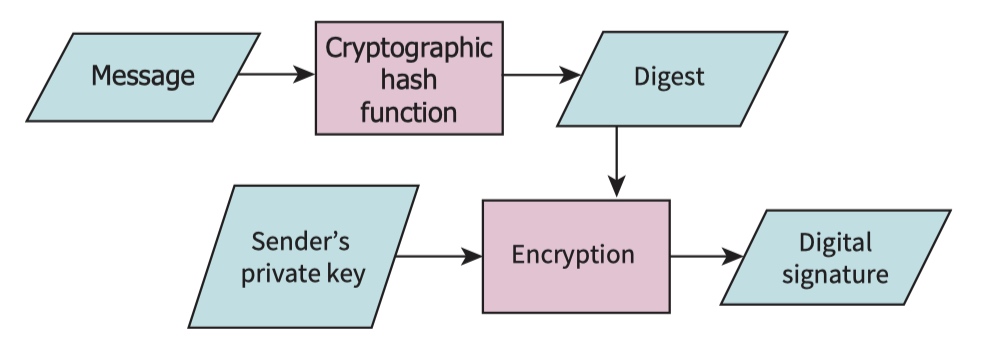
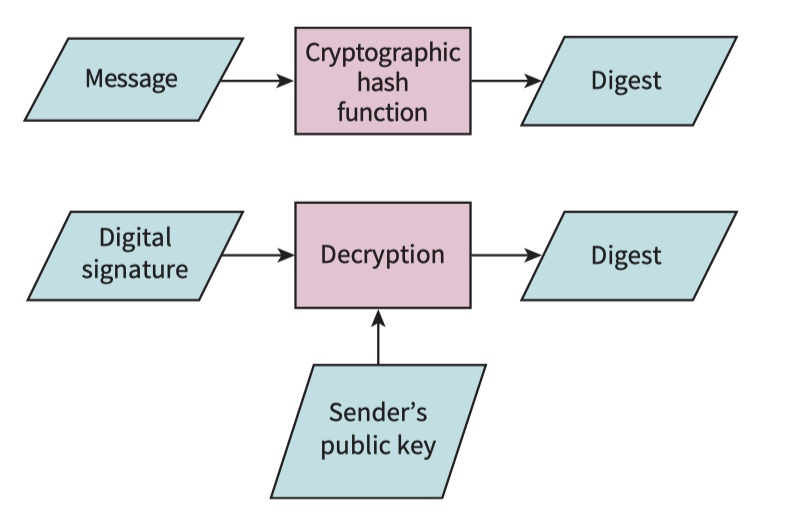
An individual can encrypt a message with a private key and send this to a recipient who has the corresponding public key and who can then use this to decrypt the received ciphertext.
Certification
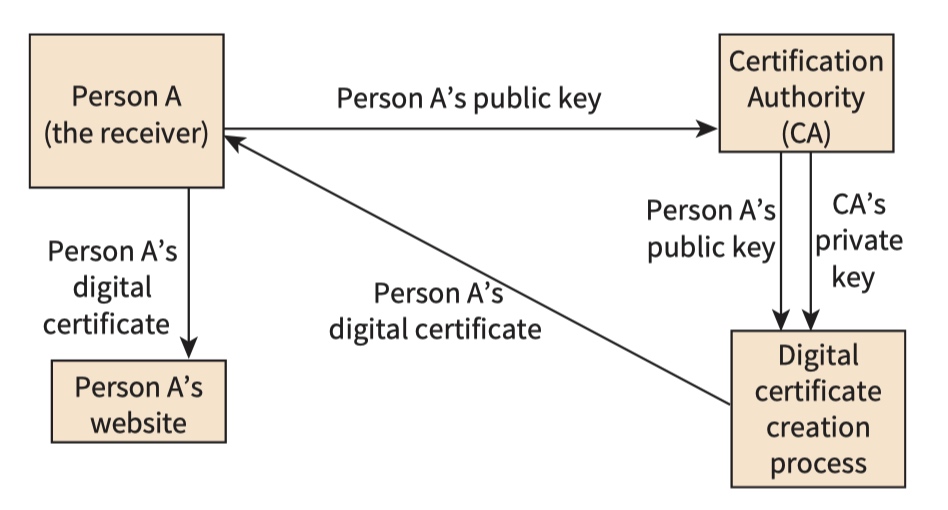
- An individual (person A) who is a would-be receiver and has a public–private key pair contacts a local CA.
- The CA confirms the identity of person A.
- Person A’s public key is given to the CA.
- The CA creates a public-key certificate (a digital certificate) and writes person A’s public key into this document.
- The CA uses encryption with the CA’s private key to add a digital signature to this document.
- The digital certificate is given to person A.
- Person A posts the digital certificate on a website.
Anyone who wishes to extract the public key from the certificate has to use the CA’s public key.
ssl certification notes:
- The starting position is someone who has a public–private key pair which are associated with a specific asymmetric key encryption algorithm.
- This person could just make the public key available to anyone who is going to be either a sender or a receiver.
- For optimum security the person instead sends the public key to a Certification Authority.
- The Certification Authority creates a digital certificate which contains the public key with proof of the ownership of the public key.
- Anyone wishing to use the public key obtains it from this digital certificate.
- A message encrypted with the public key could be sent to the owner of the private key.
- A message encrypted with the private key could be sent to anyone having the public key.
- The owner of the private key could use it to create a digital signature that could be used to authenticate an email as was suggested in Chapter 9 (Section 9.03).
21.03 Symmetric key encryption methods
加密算法
单向加密:单向加密算法是不可逆的,也就是无法将加密后的数据恢复成原始数据,除非采取碰撞攻击和穷举的方式。像是银行账户密码的存储,一般采用的就是单向加密的方式。
双向加密:可逆的,存在密文的密钥,持有密文的一方可以根据密钥解密得到原始明文,一般用于发送方和接收方都能通过密钥获取明文的情况。
双向加密包括对称加密和非对称加密。对称加密包括DES加密,AES加密等等,本文档介绍的主要是AES加密。而非对称加密包括RSA加密,ECC加密。
对称加密:指的就是加、解密使用的同是一串密钥,所以被称做对称加密。对称加密只有一个密钥作为私钥。
非对称加密:指的是加、解密使用不同的密钥,一把作为公开的公钥,另一把作为私钥。公钥加密的信息,只有私钥才能解密。反之,私钥加密的信息,只有公钥才能解密。
加密算法:
- DES 双向加密 对称加密
- AES 双向加密 对称加密
- RSA 双向加密,非对称加密
- MD5 单向加密
- SHA 单向加密
对称加密和非对称加密
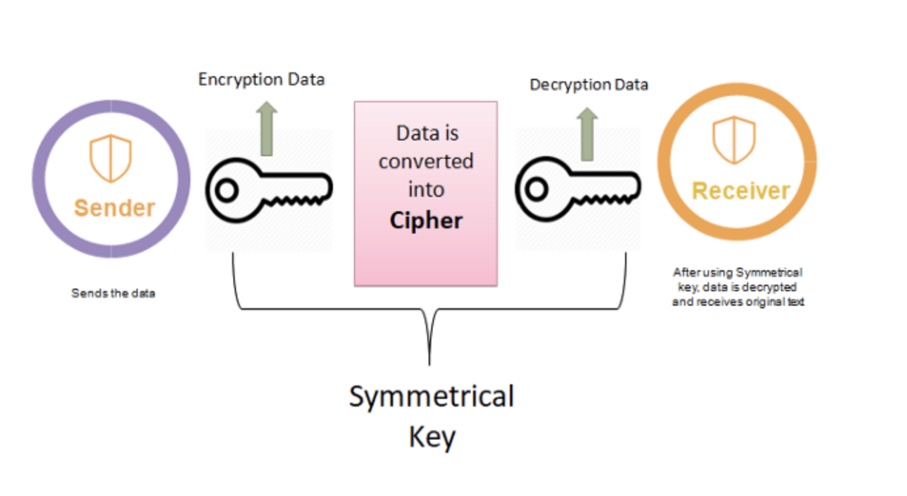
优点:加密/解密速度快,适合大数据量加密 缺点:密钥的管理与分配存在风险
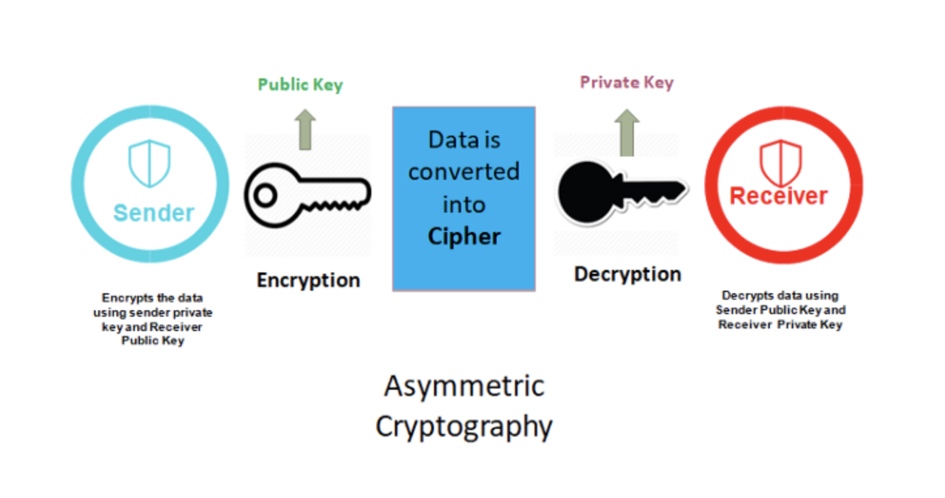
优点:安全性高,解决了对称加密的缺陷 缺点:加密和解密速度比对称密钥加密慢
应用: 数字钱包、
Symmetric key encryption methods
For many years the Data Encryption Standard (DES) was the normal choice for symmetric key encryption.
In 2001 the Advanced Encryption Standard (AES) was introduced as a superior approach.
For education purposes only a simplified DES (S-DES) was introduced which allowed the sort of operations performed in encryption to be better understood. The following is an overview of S-DES.
S-DES
S-DES is an example of a block cipher which means encrypting blocks of bits. In S-DES 8-bit blocks are encrypted. A 10-bit key is chosen. The first stage is to create two 8-bit keys from the 10-bit key. The first step in this first stage is a permutation (reordering of digits) which can be illustrated by the following.
Suppose that the 10-bit key is chosen to be 0101010101
when subjected to a permutation which can be represented by 3 5 2 7 4 10 1 9 8 6
it becomes 0010110011
encryption :
- An initial permutation.
- Application of a function using the permuted code and the first encryption key.
- A switch of the first and last 4-bit parts.
- A repeat application of the function but this time with the second encryption key.
- A final permutation using the reverse of the initial permutation sequence.
21.04 Public key encryption methods
RSA 加密算法
RSA加密过程:
ciphertext=plaintextEmodN
RSA加密是对明文的E次方后除以N后求余数的过程。只要知道E和N任何人都可以进行RSA加密了,所以说E、N是RSA加密的密钥,也就是说E和N的组合就是公钥
publicKey=(E,N)
RSA 解密过程
plaintext=ciphertextDmodN
privateKey=(D,N)
生成秘钥对
求N
准备两个互质数p,q。这两个数不能太小,太小则会容易破解,将p乘以q就是N。如果互质数p和q足够大,那么根据目前的计算机技术和其他工具,至今也没能从N分解出p和q。换句话说,只要密钥长度N足够大(一般1024足矣),基本上不可能从公钥信息推出私钥信息。
N=p∗q
求L
L 是 p-1 和 q-1的最小公倍数,可用如下表达式表示
L=lcm(p−1,q−1)
求E
E必须满足两个条件:E是一个比1大比L小的数,E和L的最大公约数为1;
用gcd(X,Y)来表示X,Y的最大公约数则E条件如下:
1<E<L
gcd(E,L)=1
之所以需要E和L的最大公约数为1,是为了保证一定存在解密时需要使用的数D。现在我们已经求出了E和N也就是说我们已经生成了密钥对中的公钥了。
求D
数D是由数E计算出来的,数D必须保证足够大。D、E和L之间必须满足以下关系:
1<D<L
E∗DmodL=1
Example
为了计算方便,p q 的值取小一旦,假设:p = 17,q = 19,
则:
- 求N:N = p * q = 323;
- 求L:L = lcm(p-1, q-1)= lcm(16,18) = 144,144为16和18对最小公倍数;
- 求E:1 < E < L ,gcd(E,L)=1,即1 < E < 144,gcd(E,144) = 1,E和144互为质数,E = 5显然满足上述2个条件,故E = 5,此时公钥= (E,N)=(5,323);
- 求D:求D也必须满足2个条件:1 < D < L,E*D mod L = 1,即1 < D < 144,5 * D mod 144 = 1,显然当D= 29 时满足上述两个条件。1 < 29 < 144,5*29 mod 144 = 145 mod 144 = 1,此时私钥=(D,N)=(29,323);
- 加密:准备的明文必须是小于N的数,因为加密或者解密都要 mod N,其结果必须小于N。 假设明文 = 123,则 密文=(123的5次方)mod 323=225
- 解密:明文=(225的29次方)mod 323 =123,所以解密后的明文为123。
Public key encryption methods
RSA (Rivest-Shamir-Adleman), the usual method for public key encryption, is named after the three people who created it. The major features of the method are the key generation algorithm and the encryption function.
Key generation :
- Two very large prime numbers p and q are chosen and their product n is calculated.
- The product (p-1)(q-1) is calculated.
- A prime number e less than (p-1)(q-1) and not a factor of it is chosen (65537 is the usual choice).
- Another number d is found which satisfies the condition that the product of d times e when divided by (p-1)(q-1) gives a remainder of 1.
- The public key becomes the pair (n,e).
- The private key becomes the pair (n,d).
21.05 SSL and TLS
SSL
SSL 是“Secure Sockets Layer”的缩写,中文叫做“安全套接层”。它是在上世纪90年代中期,由网景公司设计的。(顺便插一句,网景公司不光发明了 SSL,还发明了很多 Web 的基础设施——比如“CSS 样式表”和“JS 脚本”)
为啥要发明 SSL 这个协议捏?因为原先互联网上使用的 HTTP 协议是明文的,存在很多缺点——比如传输内容会被偷窥(嗅探)和篡改、传输中被强行加入点小广告什么的。发明 SSL 协议,就是为了解决这些问题。 到了1999年,SSL 因为应用广泛,已经成为互联网上的事实标准。IETF 就在那年把 SSL 标准化。标准化之后的名称改为 TLS(是“Transport Layer Security”的缩写),中文叫做“传输层安全协议”
通常所说的 HTTPS 协议,说白了就是“HTTP 协议”和“SSL/TLS 协议”的组合。你可以把 HTTPS 大致理解为——“HTTP over SSL”或“HTTP over TLS”
SSL and TLS
two concerns:
- The first is whether or not the website is genuine.
- The second is whether we can transfer sensitive personal data to the website, for example to buy a product offered for sale on the website.
The Secure Socket Layer (SSL) protocol was created to give assurance to a website user when a client–server application is underway.
When the Secure Socket Layer protocol is implemented it functions as an additional layer between TCP in the transport layer and the application layer. When the SSL protocol is in place, the application protocol HTTP becomes HTTPS.
SSL facts concerning :
- Although SSL is referred to as a protocol, it is in fact a protocol suite.
- There is a Record Protocol that deals with the format for data transmission.
- There is also a Handshake Protocol responsible for security.
- The operation of SSL happens without any action from the user.
- The starting point for SSL implementation is a connection between the client and the server being established by TCP.
- The client browser then invokes the Handshake Protocol from the SSP suite.
- The Handshake Protocol requests from the server its SSL certificate which is a digital certificate confirming its identity.
- The server sends this SSL certificate plus its public key.
- The browser uses this public key to encrypt a key which is to be used as a one-off session key for symmetric key encryption to be used for the data transfer during the session.
- There may also be a need at this time to agree which encryption algorithms are to be used.
21.06 Quantum cryptography (Optional)
Quantum cryptography (Optional)
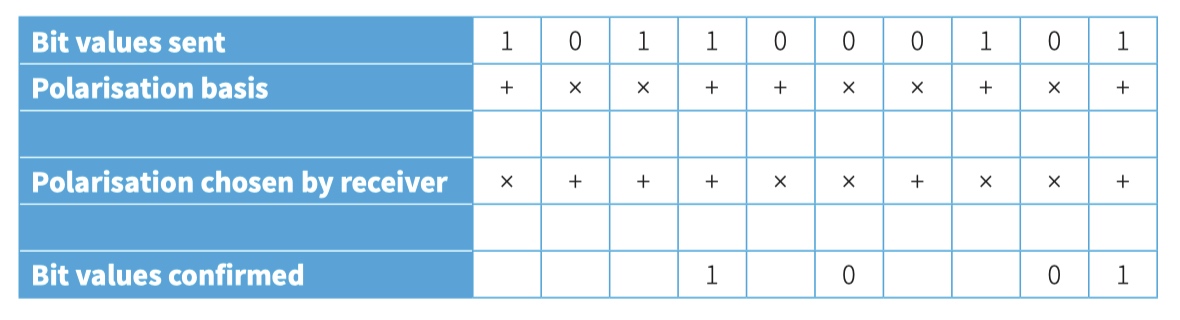
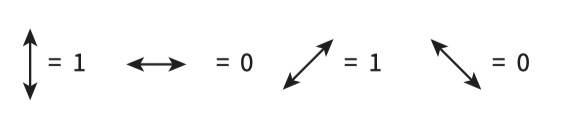
- the first row indicates the bit sent
- the second row shows the basis used for this with + representing the one using vertical and horizontal and x representing the diagonal pair.
- The third row shows the receiver’s choice for the polarisation basis for each value.