ALevel-CS Chapter 09
Security privacy and data integrity
9.01 Definitions of data integrity, privacy and security
Key Terms
- Data integrity - a requirement for data to be accurate and up to date
- Data privacy - a requirement for data to be available only to authorised users
- Data protection law - a law that relates to data privacy
- Data security - a requirement for data to be available for use when needed, ensures that only authorised users have access to the system and data can be recovered if lost or corrupted.
数据安全定义
数据完整性(data integrity): 指数据在整个生命周期中的准确性、可靠性和最终有效性。它是应防止数据库中存在不符合语义规定的数据和防止因错误信息的输入输出造成无效操作或错误信息而提出的
数据隐私(Data privacy): 秘密数据,是不想被他人获取的信息。从隐私所有者的角度,可将隐私数据分为个人隐私数据和公共隐私数据,个人隐私数据包括可用来识别或定位个人的信息(如电话号码、地址、信用卡号、认证信息等)和敏感的信息(如个人的健康状况、财务信息、历史访问记录、公司的重要文件等)
数据安全(Data security): 保护信息及信息系统免受未经授权的进入、使用、披露、破坏、修改、检视、记录及销毁。
Data integrity
Only accurate and up-to-date data has data integrity.
Data privacy
Data privacy is about keeping data private rather than allowing it to be available in the public domain.
data protection law aspects:
- The major focus relates to personal, therefore private, data that an individual supplies to an organisation.
- The data is supplied to allow the organisation to use it but only for purposes understood and agreed by the individual.
- Data protection laws oblige organisations to ensure the privacy and the integrity of this data.
- Unfortunately, having laws does not guarantee adherence to them but they do act as a deterrent if wrong-doers can be subject to legal proceedings.
Data security
The security of data has been breached if any data have been lost or corrupted.
Data security must be achieved before either data integrity or data privacy can be achieved, but data security does not by itself guarantee either data integrity or data privacy.
There are two primary aims of system security measures:
- to ensure that the system continues to carry out the tasks users need
- to ensure that only authorised users have access to the system.
9.02 Threats to the security of a computer system and of the data stored in it
Key Terms
- Malware - malicious software that has the intention of causing harm to a system or its contents
Threads to the security of a system:
- individual user not taking appropriate care
- internal mismanagement
- natural disasters
- unauthorised intrusion into the system by an individual
- malicious soft ware entering the system.
Threats to computer and data security posed by networks and the Internet
- One cause of concern is the hacker who is someone intent on gaining unauthorised access to a computer system.
- A hacker who achieves this aim might gain access to private data.
- Alternatively, a hacker might cause problems by deleting files or causing problems with the running of the system.
- The other major cause of concern is malicious soft ware entering the system.
计算机病毒 (Virus)
一旦用户下载并激活了恶意程序,病毒便会激活并破坏设备。病毒会自我复制,更改受感染设备的程序代码,并获得对设备硬件和软件组件的未经授权的控制。计算机病毒具有许多不同的结构,可用于各种网络犯罪。
当病毒将进入用户设备时,会先保持休眠状态。病毒需要触发器(即主机执行的手动操作)才能激活。通常,触发器可以是激活软件、打开受感染的文件/媒体、启用宏等。
一旦激活,该病毒就会开始搜索其他位置进行自我复制,例如在软件、硬盘驱动器、可移动硬件(如存储卡和USB驱动器)上。病毒会更改计算机程序的原始设置和代码,最后释放其有效负载。有效负载是核心代码,可使病毒能够执行其创建的任务。
网络犯罪分子创建病毒导致的结果有很多,包括:
- 使目标设备的硬件或操作系统崩溃;
- 破坏系统;
- 显示大量不需要的弹出窗口;
- 访问目标用户的联系人列表和电子邮件联系人。
蠕虫 (Worm)

蠕虫是一种可以自我复制并迅速传播到其他连接的设备、文件和软件上的恶意软件。因此,这意味着蠕虫是具有高度传染性的独立计算机程序。与需要触发才能激活的病毒不同,蠕虫是自主的,一旦被插入用户的设备中,就可以开始自我复制,不需要用户操作即可激活。
基本蠕虫会占用主机设备的过多带宽和资源,从而使其运行缓慢或无法正常运行。它还会耗尽设备的RAM和内部存储器,并使共享互联网络过载。但更糟糕的是,许多现代蠕虫通常与木马和病毒等其他类型的恶意软件配对使用。这些混合蠕虫具有以下功能:
- 提供远程访问权限;
- 加密文件;
- 发送垃圾邮件和网络钓鱼电子邮件;
- 从互联网上下载恶意软件;
- 删除文件;
- 以闪电般的速度危害主机设备。
蠕虫和木马的组合可用于执行:
- 僵尸网络攻击;
- 浏览器中间人攻击;
- 暴力攻击;
- DDoS攻击。
蠕虫是需要大量感染设备的网络攻击的理想选择。
特洛伊木马 (Trojan horse)

特洛伊木马是一种恶意软件,伪装成合法软件并诱骗用户安装它。特洛伊木马程序编写者将恶意代码插入合法软件/文件中,或者开发与合法程序类似的恶意软件。
木马无法自我复制,因此,它们会保留在本地(在其最初存储的程序/文件中)。然而,如今市场上存在将木马与病毒或蠕虫结合在一起的混合恶意软件。病毒和蠕虫为木马了提供复制功能,因此其破坏力倍增。
间谍软件 (Spyware)

在受害者不知情和未经其同意的情况下窃听受害者的行为。间谍软件是一个广义术语,包括监视用户的任何类型的恶意软件(特洛伊木马、键盘记录程序、跟踪cookie等)。
间谍软件会窃取用户的以下内容:
- 个人和职业信息;
- 登录信息;
- 支付卡号;
- 联系人列表;
- 银行信息;
- 有关其他已连接设备的信息;
- 用户系统中的漏洞等。
它还可以监视受害者的浏览行为。
当间谍软件插入公司网络或政府网站后,可能会窃听和泄漏机密数据、军事信息、商业机密、技术知识以及所有其他类型的敏感信息。
网络犯罪分子将此类信息滥用于身份盗窃、财务欺诈、勒索或引起政治动荡,还可在暗网中将此类信息出售给其他网络犯罪分子。
僵尸程序 (Bot)
僵尸程序通过聊天室,文件共享网络感染存在漏洞的计算机。这些被感染的计算机所保存的 信息都可被黑客随意取用。不论是对网络安全还是用户数据安全的保护来说,“僵尸网络”都因其极具威胁,而在国际上引起广泛关注。
僵尸网络(Botnet),是指采用一种或多种传播手段,将大量主机感染bot程序(僵尸程序),从而在控制者和被感染主机之间所形成的一个可一对多控制的网络。
Types of malware
Malware is the everyday name for malicious soft ware.
The various types of malware-containing program code are:
- virus:: tries to replicate itself inside other executable code
- worm:: runs independently and transfers itself to other network hosts
- logic bomb:: stays inactive until some condition is met
- Trojan horse:: replaces all or part of a previously useful program
- spyware:: collects information and transmits it to another system
- bot:: takes control of another computer and uses it to launch attacks.
Malware can also be classified in terms of the activity involved::
- phishing:: sending an email or electronic message from an apparently legitimate source requesting confidential information
- pharming:: setting up a bogus website which appears to be a legitimate site
- keylogger:: recording keyboard usage by the legitimate user of the system.
System vulnerability arising from user activity
Many system vulnerabilities are associated directly with the activities of legitimate users of a system. Two examples which do not involve malware are as follows.
- The use of weak passwords and particularly those which have a direct connection to the user. A poor choice of password gives the would-be hacker a strong chance of guessing the password and thus being able to gain unauthorised access.
- A legitimate user not recognising a phishing or pharming attack and, as a result, giving away sensitive information.
Typical examples of actions that might introduce malware are:
- attaching a portable storage device
- opening an email attachment
- accessing a website
- downloading a file from the Internet.
Vulnerability arising from within the system itself
Systems themselves often have security weaknesses.
- Operating systems often lack good security. Over time, there is a tendency for operating systems to increase in complexity, which leads to more opportunities for weak security.
- In the past, commonly used application packages allowed macro viruses to spread
- A very specific vulnerability is buffer overflow.
9.03 Security measures for protecting computer systems
Key Terms
- Authentication - verification of a user’s identity
- Firewall - hardware or software that monitors and controls network traffic
Disaster recovery
Such measures come under the general heading of disaster recovery contingency planning.
If an organisation has a full system always ready to replace the normally operational one, it is referred to as a ‘hot site’. By definition, such a system has to be remote from the original system to allow recovery from natural disasters such as earthquake or flood.
Safe system update
organisations may need to have the original system and its replacement running in parallel for a period to ensure continuity of service.
User authentication
The main security feature of a user account is the authentication of the user.
The normal method is to associate a password with each account.
In order for this to be effective the password needs a large number of characters including a variety of those provided in the ASCII scheme.
Alternative methods of authentication include biometric methods and security tokens.
Good pratice
- keep a personal computer secure includes not leaving the computer switched on when unattended
- not allowing someone else to observe you accessing the computer
- not writing down details of how you access it.
- Users may attach portable storage devices to a system, but this increases the risk of transferring malware into the system.
Firewall
The primary defence to malware entering a system through a network connection is to install a firewall.
A firewall can inspect the system addresses identified in the transmission of data, but can sometimes also inspect the data itself to check for anything unusual or inappropriate.
Digital signature
insist that the sender attaches a digital signature to the email.
Anti-virus software and intrusion detection
- One option is to install what is normally referred to as anti-virus soft ware but which is usually aimed at combating any type of malware.
- Another option is to install an intrusion detection system that will take as input an audit record of system use and look for examples that do not match expected system activity.
9.04 Security measures for protecting data
Key Terms
- Authorisation - definition of a user’s access rights to system components
Recovering from data loss
reasons for accidental loss of data:
- a disk or tape gets corrupted
- a disk or tape is destroyed
- the system crashes
- the file is erased or overwritten by mistake
- the location of the file is forgotten.
The principles for the procedure traditionally followed are straightforward::
- a full backup is made at regular intervals, perhaps weekly
- at least two generations of full backup are kept in storage
- incremental backups are made on a daily basis.
backup method:
- For maximum security the backup disks or tapes are stored away from the system in a fireproof and flood-proof location.
- This works well when an incremental backup occurs done overnight with the full backup handled at the weekend.
- One solution is to have a backup program that effectively freezes the file store while data is being copied.
- An alternative approach is to use a disk-mirroring strategy.
Restricting access to data
The solution is to have an authorisation policy which gives different access rights to different files for different individuals.
Protecting data content
Data can be encrypted to protect.
9.05 Data validation and verification
Key Terms
- Validation - a check that data entered is of the correct type and format; it does not guarantee that data is accurate
- Verification - confirmation of data received by a system
Data Validation
数据是任何组织最重要的资产。因此,必须不惜一切代价确保数据是有效的和可用的。数据验证(Data Validation)和数据验证(Data Verification)是确保数据具有这两种特性的两个重要过程。数据验证确保数据是干净、正确和有意义的,而数据验证则确保数据的所有副本都与原始数据一样好。因此,这两个过程都可以确保组织不会因为数据中的意外错误而损失资金。
数据验证(Data Validation)处理的是确保数据有效(干净、正确和有用)。
数据验证程序使用数据验证规则(或检查例程)来确保数据的有效性(主要是正确性和有意义)。保证了输入数据的有效性,保证了系统的安全性。
最简单的验证形式是检查输入,以确保它们由“有效”集中的字符组成。
Data Verification
数据验证是检查数据副本以确保其与原始数据副本完全相同的过程。备份数据后,通常需要进行数据验证。大多数现代备份软件都有内置的验证功能。
数据验证是一个非常重要的过程,因为它使您感到安全,因为您将确信您可以实际使用备份的数据,以防原始数据丢失或损坏。验证软件通常确保副本可读,并且内容与原始内容完全匹配。
但通常大型企业在夜间执行自动备份,因此由于验证过程而导致的时间延长并不是一个严重的问题。
Validation of data entry
Validation can only prevent incorrect data if there is an attempt to input data that is of the wrong type, in the wrong format or out of range.
Typical examples are:
- a presence check to ensure that an entry field is not left blank
- a format check, for example a date has to be dd/mm/yyyy
- a length check, for example with a telephone number
- a range check, for example the month in a date must not exceed 12
- a limit check, for example a maximum number of years for a person’s age
- a type check, for example only a numeric value for the month in a date
- an existence check, for example that a file exists with the filename referred to in the data entry.
Verification of data entry
- Double entry is one method of verification. The most common example is when a user is asked to supply a new password.
- A second method is to use a visual check of what has been entered.
Check digit
When a series of numbers are used to identify something, it is possible to use a check digit method of verification.
Verification during data transfer
It is possible for data to be corrupted during transmission. Verification techniques need to check on some property associated with the bit pattern.
Parity check

The simplest approach is to use a simple one-bit parity check.
- At the transmitting end, the number of 1s in the seven-bit code is counted.
- If the count gives an even number, the parity bit is set to 0.
- If the count gives an odd number, the parity bit is set to 1.
- This is repeated for every byte in the transmission.
- At the receiving end, the number of 1s in the eight-bit code is counted.
- If the count gives an even number, the byte is accepted.
- This is repeated for every byte in the transmission.
It is possible for two bits to be flipped in an individual byte, which would mean that the transmission is incorrect but the parity check is passed.
The limitation of the method is that it can only detect the presence of an error.
Checksum
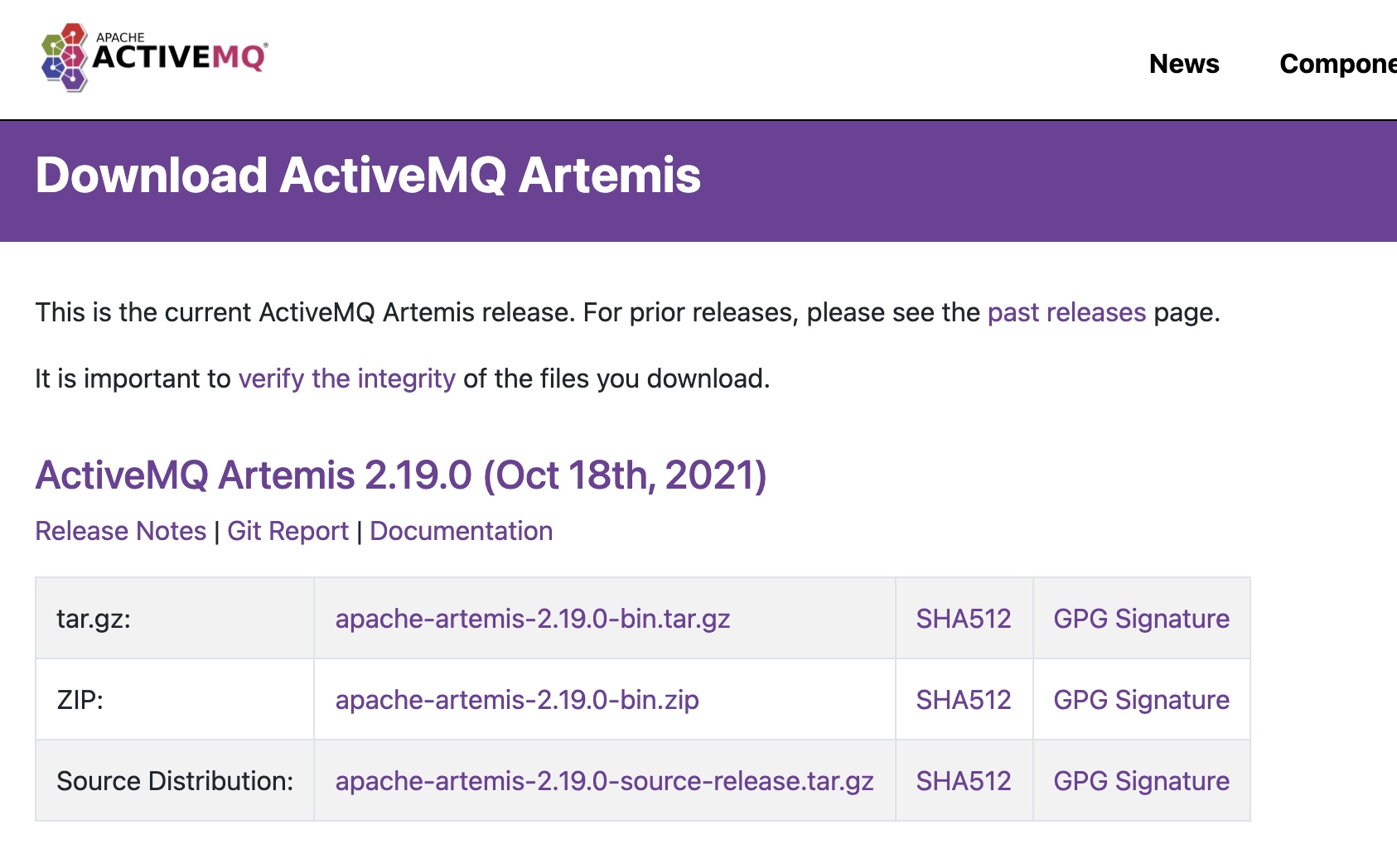
dec3227cac1eb864c1c7f229cb9b392d3fa38f5022579375fda1ba378997b166cf13e4f0182a1081c6e8592e737ac665e3b4c7fb7795646ba2122d2c9a18d550
Checksum:总和检验码,校验和。 在数据处理和数据通信领域中,用于校验目的的一组数据项的和。 这些数据项可以是数字或在计算检验总和过程中看作数字的其它字符串。 通常是以十六进制为数制表示的形式。
【作用】就是用于检查文件完整性,检测文件是否被恶意篡改,比如文件传输(如插件、固件升级包等)场景使用。
checksum
The sum of these binary numbers in a block is calculated and supplied as a checksum value in the transmission.
an error can be detected but its position in the transmission cannot be determined.