ALevel-CS Chapter 2
Communication and networking technologies
Network

2.01 The evolution of the purpose and benefits of networking
Key Terms
- Wide area network (WAN) - a network connecting computers on different sites, possibly thousands of kilometres apart
- Local area network (LAN) - a network connecting computers in a single room, in a single building or on a single site
- Client-server - an architecture where a client runs an application provided by a server on a network
- Thin-client - a client that only provides input and receives output from the application
- Thick-client - a client that carries out at least some of the processing itself
WAN AND LAN

Wide area network (WAN)
Technology was developed that allowed computers in different organisations to be networked using what would now be described as a wide area network (WAN).
benefits of WAN :
- a ‘job’ could be run on a remote computer that had the required application soft ware
- a data archive that was stored on a remote computer could be accessed
- a message could be transmitted electronically to a user on a remote computer
character of WAN :
- It will be used by an organisation or a company to connect sites or branches.
- It will not be owned by the organisation or company.
- It will be leased from a public switched telephone network company (PSTN).
- A dedicated communication link will be provided by the PSTN.
- The transmission medium will be fibre-optic cable.
- Transmission within the WAN will be from switch to switch.
- A switch will connect the WAN to each site.
- There will not be any end-systems connected directly to the WAN.
Local area network (LAN)
The computer could be a stand-alone system or some organisations chose to have more than one computer connected using a local area network (LAN).
benefits of LAN :
- The expense of installing application software on each individual PC could be saved by installing the soft ware on an application server attached to the LAN instead.
- A file server could be attached to the LAN that allowed users to store larger files and also allowed files to be shared between users.
- Instead of supplying individual printers to be connected to a user’s PC, one or more printers could be attached to a print server that was connected to the LAN; these could be higher quality printers.
- Managers in organisations could use electronic mail to communicate with staff rather than sending round memos on paper.
- The ‘paper-less office’ became a possibility, where files were to be stored in digital form on a file server rather than as paper copies in a filing cabinet.
character of LAN :
- It will be used by an organisation or a company within a site or branch.
- It will be owned by the organisation or company.
- It will be one of many individual LANS at one site.
- The transmission medium will be twisted pair cable or WiFi.
- The LAN will contain a device that allows connection to other networks.
- There will be end-systems connected which will be user systems or servers.
The Client-server Model


Client-Server 早期用于本地局域网提供内部网络服务。逐步演变为客户端浏览器模式。
Thin-client 瘦客户端 (VDI Virtual Desktop Infrastructure) :
瘦客户机的起价一般均为139美元,这是一种非常划算的标准个人电脑选择。终端用户可以通过中央数据服务器直接运行Windows®、UNIX®、Linux和服务器上的应用软件,以此来实现对应用软件的集中管理、即插即用的网络便捷性、高度安全性和可靠性,以及较低的IT支持成本。 瘦客户端除去了PC的大多数无关功能,比如CD-ROM、软驱、扩展插槽等。它们使用网络连接与中央服务器通信并向用户交付虚拟桌面,大量的业务处理不在本地硬件上进行,这有助于改进安全性。瘦客户端易于部署而且包括集中管理工具,管理员能够将策略同时应用到多个瘦客户端。
Thick-client 胖客户端

胖客户端(fat client),有时候也称为厚客户端(thick client),是在本地安装了丰富资源的网络电脑,而不是像瘦客户端那样把资源分散到网络中。比如很多PC(个人电脑)就是胖客户端,因为它们有自己的硬盘、CD/DVD光驱、软件应用程序等等。 胖客户端一致受到网络使用者的欢迎,因为胖客户端是可以定制的,使用者能够选择安装什么样的软件和配置(configuration)什么样的特殊系统。另一方面,瘦客户端容易管理,比较容易避免安全风险,并且不需要什么维修和许可开销。
The client-server model
The client-server model (or architecture) was first used in large organisations when they had installed internal networks.
The client-server mode of operation nowadays is different. The client is a web browser connected to the Internet. The server is a web server hosted on the Internet.
The server provides an application and the client uses the application.
The client-server model
A thin-client is one which :
- chooses an application to run on the server
- sends input data to the server when requested by the application
- receives output from the application.
A thick-client is one which :
- chooses an application provided by the server
- possibly carries out some processing before running the application on the server and also after receiving output from the application
- alternatively, possibly downloads the application from the server and runs the application itself.
2.02 Network topologies
Key Terms
- Topology - the configuration of a network that defines how the various devices on the network are connected
- Bus topology - contains one shared link to which all devices are attached
- End-system - a computer or server connected to a network
- Mesh topology - contains direct links between devices
- Star topology - each end-system is linked to a central device
- Hybrid network - a collection of connected LANs where some of them have different topologies or supporting technologies
- Cable:: a transmission using copper wire or fibre-optic
- Bandwidth:: a measure of the amount of data that can be transmitted per second
Network topologies
There are five requirements for a data communications system:: a sender, a receiver, a transmission medium, a message and a protocol.
Data can be sent through the medium in different modes:
- simplex mode where data flow is one-way only
- half duplex where data can flow either way but not simultaneously
- full duplex where simultaneous both-ways data flow is possible.
A ‘message’ is any type of data, which can be sent as either:
- a broadcast, which is a one-to-all communication (as used traditionally for radio and television)
- a multicast, which is from one source to many destinations
- a unicast, which is a one-to-one communication.
Network topologies
point-to-point network

Two systems are connected by a network link. Transmission might be simplex or duplex and a message can only be unicast.
bus network

Early LAN topologies used either a ring or a bus topology.
A bus topology has only one link but it is shared by a number of end-systems and is therefore described as a multi-point connection.
The topology is resilient because a fault in an end-system or in the link to it does not affect the use of the network by the other end-systems.
mesh network

each end-system has a point-to-point connection to each of the other endsystems. Transmission is duplex; messages might be unicast, multicast or broadcast.

star topology
In a star topology, each end system has a point-to-point connection to the central device.
Transmission is duplex and messages from the central device might be unicast, multicast or broadcast.
As with the bus topology, the failure of an end-system, or its link, leaves the other end-systems unaffected. However, the central device must not fail.
Currently, the star topology is the usual way to configure a network.
hybrid network
In a situation where several LANs are connected, they can have different topologies or supporting technologies. This collection of LANs then becomes a hybrid network.
2.03 Transmission media
Key Terms
- Wireless - a transmission using radio, microwave or infrared
双绞线、同轴电缆和光纤

双绞线(twisted pair)
双绞线(twisted pair,TP)是一种综合布线工程中最常用的传输介质,是由两根具有绝缘保护层的铜导线组成的。把两根绝缘的铜导线按一定密度互相绞在一起,每一根导线在传输中辐射出来的电波会被另一根线上发出的电波抵消,有效降低信号干扰的程度。

同轴电缆(Coaxial Cable)
同轴电缆(Coaxial Cable)是指有两个同心导体,而导体和屏蔽层又共用同一轴心的电缆。最常见的同轴电缆由绝缘材料隔离的铜线导体组成,在里层绝缘材料的外部是另一层环形导体及其绝缘体,然后整个电缆由聚氯乙烯或特氟纶材料的护套包住。
同轴电缆可用于模拟信号和数字信号的传输,适用于各种各样的应用,其中最重要的有电视传播、长途电话传输、计算机系统之间的短距离连接以及局域网等。同轴电缆作为将电视信号传播到千家万户的一种手段发展迅速,这就是有线电视。一个有线电视系统可以负载几十个甚至上百个电视频道,其传播范围可以达几十千米。长期以来同轴电缆都是长途电话网的重要组成部分。今天,它面临着来自光纤、地面微波和卫星的日益激烈的竞争

光纤(Fibre-optic)
光纤是光导纤维的简写,是一种由玻璃或塑料制成的纤维,可作为光传导工具。传输原理是“光的全反射”。
微细的光纤封装在塑料护套中,使得它能够弯曲而不至于断裂。通常,光纤的一端的发射装置使用发光二极管(light emitting diode,LED)或一束激光将光脉冲传送至光纤,光纤的另一端的接收装置使用光敏元件检测脉冲。
在日常生活中,由于光在光导纤维的传导损耗比电在电线传导的损耗低得多,光纤被用作长距离的信息传递。
cable

wireless

Comparing cable and wireless transmission
- The use of certain wireless transmission frequencies is regulated by government agencies and so permission has to be obtained before wireless transmission is used. (无线传输频率受政府监管)
- Outside these frequencies, no permission is needed to use the air for transmission but cables can only be laid in the ground with the permission of landowners. (电缆只能在获得土地所有者许可的情况下才能铺设)
- For global communications, the two competing technologies are:: transmission through fibre-optic cables laid underground (or on the sea bed) and satellite transmission (discussed later in this section).
- Interference is much more significant for wireless transmission and its extent is dependent on which frequencies are being used for different applications. (无线传输存在干扰)
- Repeaters are needed less often for wireless transmission. 无线传输不需要中继器
- Mobile (cell) phones now dominate Internet use and for these, only wireless transmission is possible. (手机只能使用无线传输)
- For home or small office use, wired or wireless transmission is equally efficient; often, not having to install cables favours wireless connections for a small network. (家用效率相同,但是无线传输不需要安装电缆)
2.04 LAN hardware
Key Terms
- Server - a system providing a service to end-systems
- Repeater - a device that connects two cables and provides a full-strength signal to the second cable
- Bridge - a device that connects two segments of a LAN
- Network Interface Card (NIC) - a component used to identify the end-system
- Switch - a connecting device that can send a unicast message
- Wireless Access Point (WAP) - the connecting device in a WiFi LAN
- Wireless Network Interface Card (WNIC) - provides the NIC function in a WiFi LAN
Wired LANs
Nowadays, twisted pair cables are probably the most widely used networking connections, and fibre-optic cables are becoming more common.
A bus can be extended by linking two bus cables using a repeater. A repeater is needed because over long distances, signals become attenuated (reduced in strength), making communication unreliable.
Two segments are connected using a bridge. The bridge stores the network addresses for the end-systems in the two segments it connects.
The LAN port on an end-system is connected to a Network Interface Card (NIC). The NIC is manufactured with a unique network address that is used to identify the end-system in which it has been installed.
For a star network, the central device might be a hub, a switch or a router. The switch is by far the most likely. A switch is a connecting device that can direct a communication to a specific end-system.
Wireless LANs
WiFi (WLAN in some countries) is a term used to describe wireless Ethernet.
The central device in a WiFi LAN is a Wireless Access Point (WAP).
The WAP can communicate with an end-system in the WiFi LAN provided that the end-system has a Wireless Network Interface Card (WNIC) installed.
2.05 Ethernet
以太网
以太网(Ethernet):指的是由Xerox公司创建并由Xerox,Intel和DEC公司联合开发的基带局域网规范。以太网络使用CSMA/CD(载波监听多路访问及冲突检测技术)技术,并以10M/S的速率运行在多种类型的电缆上。
它不是一种具体的网络,是一种技术规范。
以太网是当今现有局域网采用的最通用的通信协议标准。该标准定义了在局域网(LAN)中采用的电缆类型和信号处理方法。以太网在互联设备之间以10~100Mbps的速率传送信息包,双绞线电缆10 Base T以太网由于其低成本、高可靠性以及10Mbps的速率而成为应用最为广泛的以太网技术。直扩的无线以太网可达11Mbps,许多制造供应商提供的产品都能采用通用的软件协议进行通信,开放性最好。
而因特网是一个网络的网络(a network of network)。它以TCP/IP网络协议将各种不同类型、不同规模、位于不同地理位置的物理网络联接成一个整体。它也是一个国际性的通信网络集合体,融合了现代通信技术和现代计算机技术,集各个部门、领域的各种信息资源为一体,从而构成网上用户共享的信息资源网。
以太网以交换机为基础交换,因特网以路由器为基础交换。
CSMA/CD 载波监听多路访问/冲突检测
CSMA/CD即载波侦听多路访问/冲突检测,是广播型信道中采用一种随机访问技术的竞争型访问方法,具有多目标地址的特点。它处于一种总线型局域网结构,其物理拓扑结构正逐步向星型发展。CSMA/CD采用分布式控制方法,所有结点之间不存在控制与被控制的关系。
CSMA/CD的全称是Carrier Sense Multiple Access with Collision Detection,即基于冲突检测的载波监听多路访问技术。CSMA/CD也是最初802.3中的核心,应用在10M/100M的半双工有线网络中,目前CSMA/CD的应用场景少了很多,大部分都直接基于全双工工作。
节点发送数据之前需要持续监听信道,一旦节点发现信道空闲,则立刻发送数据。在发送数据的同时,节点持续监听信道,"探测" 是否有别的节点也在该时刻发送数据。
若传输过程中没有检测到别的节点的传输,那么成功传输。在成功传输后,节点需要等待帧间间隔IFG(interframe gap)时间后,可以进行下一次传输。
若在传输过程中,探测到别的节点也在传输,那么则检测到冲突。发生冲突后,节点立刻停止当前的传输,并且发送特定的干扰序列(JAM序列),用以加强该次冲突(用以保证其余所有节点都检测到该次冲突),在JAM序列发送完之后,节点随机选择一个时间倒数进行backoff。当backoff完成之后,节点可以尝试再次重传”。
以太网冲突检测过程:
- 开始 - 如果线路空闲,则启动传输,否则跳转到第4步。
- 发送 - 如果检测到冲突,继续发送数据直到达到最小回报时间(min echo receive interval)以确保所有其他转发器和终端检测到冲突,而后跳转到第4步。
- 成功传输 - 向更高层的网络协议报告发送成功,退出传输模式。
- 线路繁忙 - 持续等待直到线路空闲。
- 线路空闲 - 在尚未达到最大尝试次数之前,每隔一段随机时间转到第1步重新尝试。
- 超过最大尝试传输次数 - 向更高层的网络协议报告发送失败,退出传输模式。
Ethernet
The standard has so far evolved through five generations:: standard or traditional, fast, gigabit, 10 gigabit and 100 gigabit.
In either topology, a transmission was broadcast type. Any message would be made available to all of the end-systems without any controlled communication exchange between any pair of end-systems. For each message received an end-system had to check the destination address defined in the message to see if it was the intended recipient.
collision
- If two end-systems were to transmit messages at the same time there would be what is described as a ‘collision’.
- The method adopted for dealing with this was CSMA/CD (carrier sense multiple access with collision detection).
- This relied on the fact that if a message was being transmitted there was a voltage level on the Ethernet cable which could be detected by an end-system.
step
- Check the voltage on the transmission medium.
- If this indicates activity, wait a random time before checking again.
- If no activity is detected, start transmission.
- Continuously check for a collision.
- If no collision is detected, continue transmission.
- If a collision is detected, stop transmission of the message and transmit a jamming signal to warn all end-stations; after a random time, try again.
2.06 The Internet infrastructure
Key Terms
- Router - a device that acts as a node on the Internet
Internet Service Provider (ISP)
The initial function of an Internet Service Provider (ISP) was to give Internet access to an individual or company.
Router
We can also think of the Internet in terms of the connections that carry the most traffic, which consist of a set of fibre-optic cables laid under the sea and across land, which can be described as a ‘mesh’ structure.
Each router is connected to several other routers and its function is to choose the best route for a transmission.
Public switched telephone network (PSTN)

digital data could be transmitted provided that a modem was used to convert the digital data to analogue signals.
an organisation could instead pay for a leased line service that provided a dedicated, permanently connected link with guaranteed transmission speed.
More recently, the PSTNs have upgraded their main communication lines to fibre-optic cable employing digital technology.
Cell phone network
The mobile phone, equipped with the appropriate software, communicates with a standard cell tower to access the wireless telephone network, which in turn provides a connection to the Internet.
2.07 Applications that make use of the Internet
Key Terms
- Private cloud - owned by and only accessed by an organisation
- Public cloud - owned by a cloud service provider for general access
- On-demand - when the bit stream content is transmitted at a time chosen by the user
- Real-time - when the bit stream content is transmitted as it is produced
- Bit rate - the number of bits transmitted per second
The World Wide Web (WWW)
The Internet is, as has been described above, an Internetwork.
By contrast, the World Wide Web (WWW) is a distributed application which is available on the Internet.
the web consists of an enormous collection of websites each having one or more web pages. The special feature of a web page is that it can contain hyperlinks which, when clicked, give direct and essentially immediate access to other web pages.
Cloud computing
Cloud computing is the provision of computing services usually via the Internet. An organisation may choose to establish its own private cloud.
The alternative is a public cloud. This is created, managed and owned by a third-party cloud service provider.
Service::
- infrastructure provision - IaaS - Infrastructure as a service
- platform provision - PaaS - Platform as a service
- software provision - SaaS - Software as a Service
advantages
- For the infrastructure provision, the advantages include the better performance when running software and the increased storage capacity.
- For the platform provision, the cloud can offer facilities for software development and testing.
- For the software provision, the cloud will be able to run applications that require high performance systems. Alternatively, it could be that the costs to a company of buying and installing a software package themselves would be far too high.
- Regard to outsourcing. The cloud user no longer needs technical expertise.
disadvantages
The cloud service provider has complete access to all of the data stored on the cloud. The cloud user cannot be sure that their data is not being shared with third-parties.
The cloud service provider is being relied on to ensure data cannot be lost.
Bit streaming
Streaming media make use of the Internet for leisure activities like listening to music or watching a video. Because of the file sizes involved, streamed media is always compressed to a sequence of bits - a ‘bit stream’.
on demand - In this case the delivery of the media and the playing of the media are two separate processes. The incoming media data are received into a buffer created on the user’s computer. The user’s machine has media player software that takes the media data from the buffer and plays it.
real-time(live transmission)- the content is being generated as it is being delivered such as when viewing a sporting event.
bit rate - The process of delivering the content is determined by the bit rate. example 300kbps or 128kbps
2.08 IP addressing
Key Terms
- IPv4 address - a 32-bit long, hierarchical address of a device on the Internet
IPv4 addressing
three classes of IPv4 address

Currently the Internet uses Internet Protocol version 4 (IPv4) addressing.
The IPv4 addressing scheme is based on 32 bits (four bytes) being used to define an IPv4 address. The 32 bits allow 2 32different addresses.
The original addressing scheme was designed on the basis of a hierarchical address with a group of bits defining a network (a netID) and another group of bits defining a host on that network (a hostID).
Classless inter-domain routing (CIDR)

CIDR retains the concept of a netID and a hostID but removes the rigid structure and allows the split between the netID and the hostID to be varied to suit individual need.
11 bit remaining hostIDs allowing 2048 hosts
Sub-netting

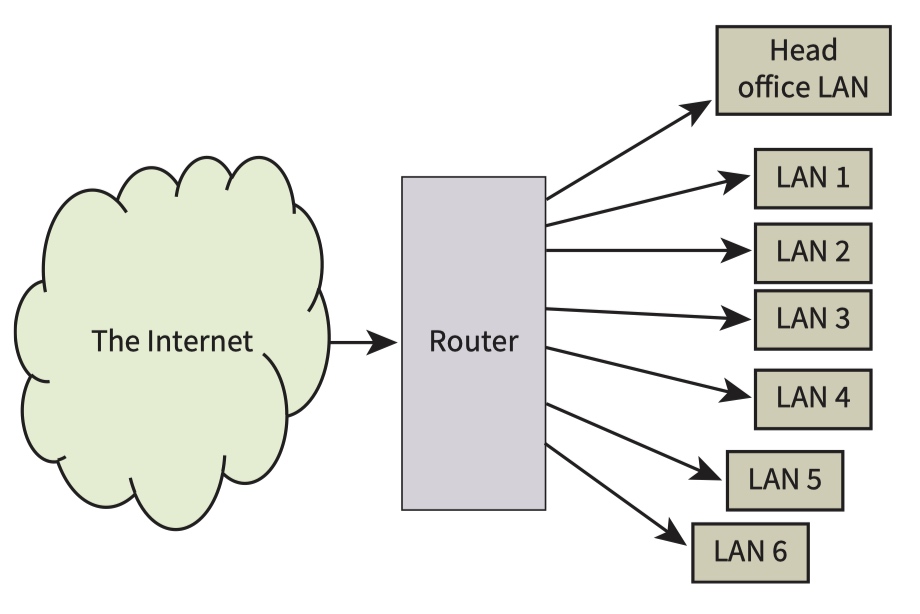
For the connection to the Internet the gateway would either first connect to a router or have the capability to act as a router itself.
On the Internet, all of the allocated IP addresses have a netID pointing to the router. The router then has to interpret the hostID to direct the transmission to the appropriate workstations on one of the LANS via a gateway.
Network address translation (NAT)

Sub-routing deviates from the principle that every IP address should be unique.
The solution for dealing with the addressing is to use network address translation (NAT)
The NAT box has one IP address which is visible over the Internet and so can be used as a sending address or as a receiving address.
Static and dynamic IP addresses
The ISP will have available a large number of hostIDs. However, the number of users that the ISP is supporting could very likely be larger than the total number of addresses available. Fortunately for the ISP and for an individual user many of these potential users will not be engaged in Internet interaction. The normal practice is for the ISP to create a ‘dynamic address’ for a user.
The alternative is a ‘static address’ which never changes and can be provided if a user is prepared to pay an extra charge.
IPv6 addressing

IP version 6 (IPv6) uses a 128bit addressing scheme allowing 2 128different addresses
2.09 Domain names
Key Terms
- Domain name service (DNS) - a hierarchical distributed database installed on domain name servers that is responsible for mapping a domain name to an IP address. Also known as domain name system.
Domain names
The domain name service (DNS) service allocates readable domain names for Internet hosts and provides a system for finding the IP address for an individual domain name.
There are more than 250 top-level domains which are either generic (e.g. .com, .edu, and .gov) or represent countries (e.g. .uk and .nl).
The domain name is included in a universal resource locator (URL), which identifies a web page, or an email address.
name resolution:
- If the domain is under the control of the server to which the query is sent then an authoritative and correct IP address is returned.
- If the domain is not under the control of the server, an IP address can still be returned if it is stored in a cache of recently requested addresses but it might be out of date.
- If the domain in the query is remote then the query is sent to a root server which can provide an address for the name server of the appropriate top-level domain. This in turn can provide the address for the name server in the next lower domain. This continues until the query reaches a name server that can provide an authoritative IP address.